What Is Ethereum’s Role in Smart Contracts?
Ethereum has become a cornerstone of blockchain technology, especially when it comes to enabling smart contracts. These self-executing agreements are transforming how transactions and digital interactions occur across various industries. Understanding Ethereum’s role in this ecosystem is essential for anyone interested in blockchain innovation, decentralized applications (dApps), or the future of digital finance.
How Ethereum Supports Smart Contracts
At its core, Ethereum provides a decentralized platform that allows developers to create and deploy smart contracts without relying on centralized authorities. Unlike traditional contracts that require intermediaries like lawyers or banks, smart contracts on Ethereum automatically execute predefined rules once certain conditions are met. This automation reduces costs, increases transparency, and minimizes the risk of manipulation.
Ethereum's blockchain acts as an immutable ledger where these contracts are stored and executed. Once deployed, they run exactly as programmed—no third-party intervention needed—ensuring trustless interactions between parties. This feature makes Ethereum particularly appealing for applications requiring high security and transparency.
Programming Languages Powering Smart Contracts
One of the key strengths of Ethereum is its support for specialized programming languages designed explicitly for writing smart contracts. Solidity is by far the most popular language used within the ecosystem; it resembles JavaScript in syntax but offers features tailored to blockchain development.
Developers can craft complex logic within their smart contracts using Solidity, enabling functionalities such as token creation (ERC-20 tokens), voting mechanisms, financial derivatives, or even gaming logic. The flexibility provided by these languages allows for innovative use cases across sectors like finance (DeFi), gaming (NFTs), supply chain management, and more.
Gas Fees: The Cost of Running Smart Contracts
Executing smart contracts on Ethereum isn’t free; it involves paying gas fees measured in Ether (ETH). Gas represents computational effort required to process transactions or contract executions on the network. When users initiate a transaction involving a smart contract—say transferring tokens or executing a DeFi trade—they must pay an amount proportional to the complexity involved.
This fee mechanism helps prevent spam attacks but also introduces considerations around cost efficiency during periods of high network congestion. Recent upgrades aim to optimize gas consumption while maintaining security standards—a critical factor influencing user adoption and developer activity.
Smart Contracts’ Role in Decentralized Applications
Smart contracts form the backbone of decentralized applications (dApps). These apps operate without central servers; instead, they rely entirely on code running securely on blockchains like Ethereum. From simple token swaps via platforms like Uniswap to complex lending protocols such as Aave or Compound—these dApps leverage smart contract logic extensively.
The ability to automate processes ensures that dApps can offer services with increased transparency and reduced reliance on intermediaries—a significant advantage over traditional centralized systems. As a result, industries ranging from finance to entertainment have embraced this technology for creating innovative solutions that prioritize user control over assets and data.
Security Challenges Associated With Smart Contracts
While offering numerous benefits—including automation and decentralization—smart contracts also pose security risks if not properly coded or audited. Bugs within contract code can lead to vulnerabilities exploitable by hackers; notable incidents include The DAO hack in 2016 which resulted in millions lost due to flawed code execution.
To mitigate these risks:
- Developers conduct thorough audits before deployment.
- Specialized firms provide security assessments.
- Formal verification methods are increasingly adopted.
Despite advancements in security practices, vulnerabilities remain possible due to human error or unforeseen edge cases within complex logic structures.
Scalability Issues And Upgrades Like Ethereum 2.0
As demand grows for dApps built atop Ethereum’s platform—including DeFi projects and NFTs—the network faces scalability challenges limiting transaction throughput and increasing fees during peak times. To address this:
- Ethereum 2.x aims at transitioning from proof-of-work (PoW) consensus mechanisms toward proof-of-stake (PoS).
- It introduces sharding techniques allowing parallel processing across multiple chains.
These upgrades promise faster transaction speeds with lower costs while enhancing overall network security—a crucial step toward mainstream adoption of blockchain-based solutions involving smart contracts.
Layer 2 Solutions Enhancing Performance
In addition to core upgrades:
- Layer 2 solutions such as Polygon (formerly Matic), Optimism, Arbitrum facilitate off-chain processing.
- They enable faster transactions at reduced costs by batching operations before settling them back onto mainnet.
These innovations help bridge current performance gaps until full-scale upgrades mature.
Regulatory Environment And Its Impact On Smart Contract Adoption
Legal frameworks surrounding blockchain technology continue evolving worldwide—and their influence directly affects how businesses develop with smart contracts on platforms like Ethereum:
- Governments seek clarity around issues such as securities classification for tokens created via smart contract protocols.
- Regulatory uncertainty may hinder innovation if overly restrictive policies emerge.
Conversely:
- Clear guidelines foster trust among users,
- Encourage institutional participation,
- Promote responsible development practices aligned with legal standards.
Importance Of Compliance And Auditing
Given potential legal implications:
- Regular audits ensure compliance with applicable regulations,
- Transparent documentation builds user confidence,3.. Collaboration between developers & regulators promotes sustainable growth.
Future Outlook: Risks And Opportunities
Despite impressive progress made through recent updates like ETH 2.x enhancements:
Risks remain, including:
- Security vulnerabilities leading potentially catastrophic losses,
- Regulatory uncertainties stalling broader adoption,
- Environmental concerns related mainly to energy-intensive proof-of-work models,
Opportunities abound through ongoing innovations:
1.. Continued scalability improvements will make dApps more accessible globally,2.. Growing sectors such as DeFi & NFTs expand use cases leveraging robust smart contract capabilities,3.. Increasing regulatory clarity could accelerate institutional involvement,
By balancing technological advancements with rigorous security measures—and aligning developments with evolving legal landscapes—Ethereum continues shaping its pivotal role at the heart of modern decentralized ecosystems.
Understanding how Ethereum supports intelligent automation through secure & scalable infrastructure reveals why it's considered foundational within blockchain technology today—and why ongoing developments will determine its future trajectory amidst emerging challenges & opportunities alike


JCUSER-IC8sJL1q
2025-05-09 12:40
What is Ethereum’s role in smart contracts?
What Is Ethereum’s Role in Smart Contracts?
Ethereum has become a cornerstone of blockchain technology, especially when it comes to enabling smart contracts. These self-executing agreements are transforming how transactions and digital interactions occur across various industries. Understanding Ethereum’s role in this ecosystem is essential for anyone interested in blockchain innovation, decentralized applications (dApps), or the future of digital finance.
How Ethereum Supports Smart Contracts
At its core, Ethereum provides a decentralized platform that allows developers to create and deploy smart contracts without relying on centralized authorities. Unlike traditional contracts that require intermediaries like lawyers or banks, smart contracts on Ethereum automatically execute predefined rules once certain conditions are met. This automation reduces costs, increases transparency, and minimizes the risk of manipulation.
Ethereum's blockchain acts as an immutable ledger where these contracts are stored and executed. Once deployed, they run exactly as programmed—no third-party intervention needed—ensuring trustless interactions between parties. This feature makes Ethereum particularly appealing for applications requiring high security and transparency.
Programming Languages Powering Smart Contracts
One of the key strengths of Ethereum is its support for specialized programming languages designed explicitly for writing smart contracts. Solidity is by far the most popular language used within the ecosystem; it resembles JavaScript in syntax but offers features tailored to blockchain development.
Developers can craft complex logic within their smart contracts using Solidity, enabling functionalities such as token creation (ERC-20 tokens), voting mechanisms, financial derivatives, or even gaming logic. The flexibility provided by these languages allows for innovative use cases across sectors like finance (DeFi), gaming (NFTs), supply chain management, and more.
Gas Fees: The Cost of Running Smart Contracts
Executing smart contracts on Ethereum isn’t free; it involves paying gas fees measured in Ether (ETH). Gas represents computational effort required to process transactions or contract executions on the network. When users initiate a transaction involving a smart contract—say transferring tokens or executing a DeFi trade—they must pay an amount proportional to the complexity involved.
This fee mechanism helps prevent spam attacks but also introduces considerations around cost efficiency during periods of high network congestion. Recent upgrades aim to optimize gas consumption while maintaining security standards—a critical factor influencing user adoption and developer activity.
Smart Contracts’ Role in Decentralized Applications
Smart contracts form the backbone of decentralized applications (dApps). These apps operate without central servers; instead, they rely entirely on code running securely on blockchains like Ethereum. From simple token swaps via platforms like Uniswap to complex lending protocols such as Aave or Compound—these dApps leverage smart contract logic extensively.
The ability to automate processes ensures that dApps can offer services with increased transparency and reduced reliance on intermediaries—a significant advantage over traditional centralized systems. As a result, industries ranging from finance to entertainment have embraced this technology for creating innovative solutions that prioritize user control over assets and data.
Security Challenges Associated With Smart Contracts
While offering numerous benefits—including automation and decentralization—smart contracts also pose security risks if not properly coded or audited. Bugs within contract code can lead to vulnerabilities exploitable by hackers; notable incidents include The DAO hack in 2016 which resulted in millions lost due to flawed code execution.
To mitigate these risks:
- Developers conduct thorough audits before deployment.
- Specialized firms provide security assessments.
- Formal verification methods are increasingly adopted.
Despite advancements in security practices, vulnerabilities remain possible due to human error or unforeseen edge cases within complex logic structures.
Scalability Issues And Upgrades Like Ethereum 2.0
As demand grows for dApps built atop Ethereum’s platform—including DeFi projects and NFTs—the network faces scalability challenges limiting transaction throughput and increasing fees during peak times. To address this:
- Ethereum 2.x aims at transitioning from proof-of-work (PoW) consensus mechanisms toward proof-of-stake (PoS).
- It introduces sharding techniques allowing parallel processing across multiple chains.
These upgrades promise faster transaction speeds with lower costs while enhancing overall network security—a crucial step toward mainstream adoption of blockchain-based solutions involving smart contracts.
Layer 2 Solutions Enhancing Performance
In addition to core upgrades:
- Layer 2 solutions such as Polygon (formerly Matic), Optimism, Arbitrum facilitate off-chain processing.
- They enable faster transactions at reduced costs by batching operations before settling them back onto mainnet.
These innovations help bridge current performance gaps until full-scale upgrades mature.
Regulatory Environment And Its Impact On Smart Contract Adoption
Legal frameworks surrounding blockchain technology continue evolving worldwide—and their influence directly affects how businesses develop with smart contracts on platforms like Ethereum:
- Governments seek clarity around issues such as securities classification for tokens created via smart contract protocols.
- Regulatory uncertainty may hinder innovation if overly restrictive policies emerge.
Conversely:
- Clear guidelines foster trust among users,
- Encourage institutional participation,
- Promote responsible development practices aligned with legal standards.
Importance Of Compliance And Auditing
Given potential legal implications:
- Regular audits ensure compliance with applicable regulations,
- Transparent documentation builds user confidence,3.. Collaboration between developers & regulators promotes sustainable growth.
Future Outlook: Risks And Opportunities
Despite impressive progress made through recent updates like ETH 2.x enhancements:
Risks remain, including:
- Security vulnerabilities leading potentially catastrophic losses,
- Regulatory uncertainties stalling broader adoption,
- Environmental concerns related mainly to energy-intensive proof-of-work models,
Opportunities abound through ongoing innovations:
1.. Continued scalability improvements will make dApps more accessible globally,2.. Growing sectors such as DeFi & NFTs expand use cases leveraging robust smart contract capabilities,3.. Increasing regulatory clarity could accelerate institutional involvement,
By balancing technological advancements with rigorous security measures—and aligning developments with evolving legal landscapes—Ethereum continues shaping its pivotal role at the heart of modern decentralized ecosystems.
Understanding how Ethereum supports intelligent automation through secure & scalable infrastructure reveals why it's considered foundational within blockchain technology today—and why ongoing developments will determine its future trajectory amidst emerging challenges & opportunities alike
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
Two leading Federal Reserve chair candidates are advocating aggressive rate cuts despite inflation concerns, potentially creating powerful tailwinds for cryptocurrency markets. With Trump considering 11 candidates to replace Jerome Powell in May 2026, dovish monetary policy could drive substantial crypto gains.
🏛️ Leading Dovish Candidates:
-
Marc Sumerlin: Former Bush admin economist advocating 50+ basis point cuts
David Zervos: Jefferies Chief Market Strategist supporting 200+ basis point total reduction
Key Position: Both believe current monetary policy is "offensively tight" despite PPI data
Trump Alignment: Both support lower borrowing costs and economic stimulus
📈 How Rate Cuts Boost Crypto:
-
Lower Opportunity Costs: Reduced bond/savings yields push investors toward crypto
Increased Liquidity: More money flowing into alternative investments
Dollar Weakness: Makes Bitcoin more attractive as store of value
Risk Appetite: Cheaper borrowing costs encourage higher-yield asset allocation
Historical Precedent: 2020-2021 crypto rally coincided with Fed accommodation
💎 Crypto Market Benefits:
-
Bitcoin: Enhanced digital store of value appeal during dollar weakness
Ethereum: Increased DeFi activity from improved liquidity conditions
Layer-1 Protocols: More developer activity and ecosystem growth
Infrastructure: Crypto companies access cheaper capital for expansion
Stablecoins: Expanded usage in lower-rate environments
🔍 Selection Process Impact:
-
11 Candidates: Diverse backgrounds from Fed officials to market strategists
Timeline: Prolonged uncertainty could create short-term volatility
Market Experience: Candidates like Zervos bring crypto-aware perspectives
Policy Clarity: Dovish positioning provides directional support regardless of final pick
📊 Historical Correlation:
-
2022 Struggle: Crypto fell as rates rose aggressively
2023-2024 Recovery: Crypto rallied as rate hikes peaked and cuts expected
Transmission Speed: Crypto markets react immediately to Fed policy changes
Sustained Impact: Rate cut campaigns provide ongoing support over months
⚠️ Key Considerations:
-
Regulatory uncertainty remains despite monetary tailwinds
Timing matters - gradual vs aggressive cuts create different market dynamics
Fed chair's approach to financial stability could impact crypto oversight
Monetary policy alone cannot drive sustained crypto adoption
🎯 Investment Implications: The combination of dovish Fed leadership and Trump's pro-crypto stance creates potentially explosive conditions for digital assets. Lower rates reduce competition from traditional investments while institutional appetite for alternatives increases dramatically.
Bottom Line: Fed chair candidates advocating aggressive rate cuts could unleash massive liquidity into crypto markets. Historical data shows strong correlations between accommodative monetary policy and crypto rallies. The May 2026 appointment could mark a pivotal moment for digital asset adoption.
Read the complete analysis on Fed chair candidates and crypto market implications: 👇 https://blog.jucoin.com/fed-chair-rate-cuts-crypto/?utm_source=blog
#FedChair #RateCuts #Crypto #Bitcoin #Ethereum


JU Blog
2025-08-16 08:50
💰 Fed Chair Rate Cuts Could Spark Massive Crypto Rally
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
📰 Điều gì đang thúc đẩy đà tăng của Ethereum — Và liệu nó có thể kéo dài? 🚀
Xem chia sẻ của Jucoin CEO Sammi Li về chủ đề này trên DecryptMedia 👇🏻
🔗 https://decrypt.co/335292/whats-driving-ethereums-surge-and-can-it-last
#JuCoin #JucoinVietnam #Ethereum #ETH #Blockchain


Lee | Ju.Com
2025-08-15 06:24
📰 Điều gì đang thúc đẩy đà tăng của Ethereum — Và liệu nó có thể kéo dài? 🚀
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
📰 Tom Lee đặt mục tiêu #Ethereum đạt 15,000 USD vào năm 2025, nhờ vào kho $ETH kỷ lục 5 tỷ USD của #BitMine. Chiến lược này tận dụng tăng trưởng #Stablecoin từ 250 tỷ USD lên 2 nghìn tỷ USD và 60% thị phần của #Ethereum trong mảng token hóa tài sản thực.
🔎 Đọc thêm: https://blog.jucoin.com/tom-lee-ethereum-prediction/
#JuCoin #JucoinVietnam #JucoinInsight #Ethereum #ETH #Crypto #Blockchain #CryptoNews #PricePrediction #Tokenization #Stablecoin


Lee | Ju.Com
2025-08-15 06:25
🌟Jucoin Insight | Dự đoán giá #Ethereum của Tom Lee: Mục tiêu 15,000 USD vào 2025! 🚀
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
The crypto market experienced significant losses in August 2025, with most major tokens posting notable declines. Here's what's driving the downturn and what investors need to know:
💰 Major Losses Overview:
-
Bitcoin (BTC): -8% to $113,562
Ethereum (ETH): -5.2% to $4,166
Cardano (ADA): -6.3% to $0.8526
XRP: -3.77% to $2.89
Dogecoin (DOGE): -2.21% to $0.2127
🎯 Key Market Drivers:
1️⃣ Jackson Hole Uncertainty: Fed rate cut expectations dropped from 98% to 15%, dampening institutional risk appetite
2️⃣ ETF Volatility: Ethereum ETFs saw $196.6 million outflows after a record $2.8 billion inflow the previous week
3️⃣ Regulatory Delays: Stalled altcoin ETF approvals and unclear stablecoin legislation adding market anxiety
4️⃣ Technical Liquidations: Over $1.2 billion in long positions liquidated as Bitcoin hit resistance at $124,000
🚨 Security Concerns:
-
AI-powered wallet drainers targeting developers
$2.17 billion in crypto hacks recorded in 2025
GreedyBear exploit affecting 150+ fake browser extensions
🏆 Biggest Altcoin Losers (24h):
-
Gari Network (GARI): -23.15%
Useless Coin (USELESS): -17.98%
League of Kingdoms Arena (LOKA): -10.03%
Livepeer (LPT): -9.90%
💡 What's Next:
-
All eyes on Powell's Jackson Hole speech for Fed policy signals
ETF flows remain key indicator for short-term price action
Most analysts view this as temporary correction, not trend reversal
Long-term fundamentals remain intact despite current volatility
The market correction appears driven by macro uncertainty rather than fundamental crypto weaknesses. Investors are consolidating positions ahead of key policy announcements.
Read the complete market analysis with detailed charts and expert insights: 👇 https://blog.jucoin.com/crypto-losses-recent-key-market-declines-explained/
#CryptoLosses #Bitcoin #Ethereum


JU Blog
2025-08-20 10:37
📉 Crypto Market Takes Sharp Hit: Major Tokens Down 3-8% This Week
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
n a landmark Bankless interview marking Ethereum's 10th anniversary, co-founder Vitalik Buterin unveiled his comprehensive roadmap transforming Ethereum from "world computer" to "world ledger" - the platform that stores civilization's assets and records.
💰 Key Vision Highlights:
-
Identity Evolution: Clear pivot to "world ledger" positioning for institutional adoption
Privacy Revolution: ZK-powered privacy becomes DEFAULT, not optional
Massive Scaling: 10,000 TPS on Layer 1 through ZK-proof verification
Treasury Strategy: Cautious support for ETH treasury companies worth $12B
🎯 Technical Roadmap:
1️⃣ ZK-EVM Integration: Complete within one year for simplified verification 2️⃣ Privacy-by-Default: Direct wallet integration eliminating specialized privacy apps 3️⃣ Protocol Simplification: Reduced complexity while preserving programmability 4️⃣ Gas Limit Scaling: Progressive increases toward 10,000 TPS capacity
🏆 Revolutionary Features Coming:
-
Privacy Wallets: Seamless public/private balance management in MetaMask
Scalable Privacy Pools: Exclude bad actors while protecting legitimate users
Cross-L2 Interoperability: Minutes instead of hours for withdrawals
Hardware Accessibility: Even "$7 Raspberry Pi" can validate ZK-proofs
💡 Strategic Insights:
-
Barbell Strategy: L1 optimized for security, L2 for performance and UX
Quantum Resistance: Post-quantum cryptography implementation planned
Cypherpunk Renaissance: Return to original privacy-focused values
Conservative Leverage: Warning against overleveraged ETH treasury risks
🔥 Market Implications:
With BlackRock endorsing Ethereum as the "master ledger for the world" and 3.04 million ETH ($12B) held by treasury companies, Buterin's vision positions Ethereum as foundational global infrastructure while maintaining decentralized ethos.
The transition from experimental platform to civilization-scale registry represents the next phase of blockchain adoption - moving beyond speculation toward real economic utility.
Read the complete technical analysis and implementation timeline: 👇 https://blog.jucoin.com/vitalik-buterin-ethereum-world-ledger-vision/
#Ethereum #VitalikButerin #ETH


JU Blog
2025-08-13 07:46
🚀 Vitalik Buterin Reveals Ethereum's "World Ledger" Vision for the Next Decade!
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
What is Account Abstraction (EIP-4337)?
Understanding Ethereum Accounts and Their Limitations
Ethereum, the leading blockchain platform for decentralized applications, has traditionally relied on two main types of accounts: externally owned accounts (EOAs) and contract accounts. EOAs are controlled by private keys and are used by users to send transactions, while contract accounts are governed by smart contracts that execute code autonomously. However, this binary structure presents certain limitations in terms of flexibility, security, and user experience.
For example, EOAs require users to manage private keys securely—an often complex task that can lead to loss of funds if mishandled. Contract accounts lack the ability to perform certain operations without external triggers or specific transaction structures. As Ethereum's ecosystem expands into areas like DeFi (Decentralized Finance), NFTs (Non-Fungible Tokens), and enterprise solutions, these constraints hinder seamless user interactions and advanced functionalities.
This context has driven the development of Account Abstraction, a concept aimed at redefining how Ethereum accounts function—making them more versatile and adaptable to modern needs.
What Is Account Abstraction?
Account abstraction refers to a paradigm shift in Ethereum's account model that allows for more flexible account behaviors beyond simple storage of Ether or tokens. Instead of being limited to basic transaction validation via private keys, abstracted accounts can incorporate custom logic for authorization, multi-signature schemes, social recovery mechanisms, or even biometric authentication.
Specifically related to EIP-4337—a prominent proposal within this space—it introduces a new layer where user operations are processed differently from traditional transactions. This enables users to execute complex actions without relying solely on externally owned wallets or traditional smart contracts as intermediaries.
In essence, account abstraction aims to make blockchain interactions more intuitive while enhancing security features such as multi-factor authentication or time-locks directly integrated into account logic.
The Context Behind EIP-4337 Development
The push towards account abstraction stems from several challenges faced by the Ethereum community:
User Experience: Managing private keys is cumbersome for many users; losing access means losing funds.
Security Risks: Private key management exposes vulnerabilities; compromised keys lead directly to asset theft.
Smart Contract Limitations: Existing models do not support advanced features like social recovery or flexible authorization schemes natively.
Scalability & Usability Needs: As DeFi grows exponentially with millions engaging in financial activities on-chain — there’s a pressing need for smarter account management systems that can handle complex workflows efficiently.
In response these issues have prompted proposals like EIP-4337 which aim at creating an improved framework where user operations can be processed more flexibly while maintaining compatibility with existing infrastructure.
Key Features of EIP-4337
Introduced in 2021 by members of the Ethereum community through extensive discussions and development efforts, EIP-4337 proposes several core innovations:
Abstract Accounts & Signers
The proposal introduces two primary components:
- Abstract Accounts: These are enhanced wallet-like entities capable of executing arbitrary transactions based on custom logic embedded within them.
- Abstract Signers: They facilitate signing transactions without exposing sensitive details—enabling features like multi-signature requirements seamlessly integrated into the account itself rather than relying solely on external wallets.
Improved Security Mechanisms
EIP-4337 emphasizes security enhancements such as:
- Multi-signature requirements ensuring multiple approvals before executing critical actions.
- Time-locks preventing immediate transfers—adding layers against unauthorized access.
- Social recovery options allowing trusted contacts or mechanisms restoring access if private keys are lost.
Compatibility & Transition
A significant aspect is backward compatibility with existing Ethereum infrastructure—meaning developers can adopt new features gradually without disrupting current applications or wallets during transition phases.
Recent Progress and Community Engagement
Since its proposal in 2021:
- The idea has gained substantial support among developers aiming at making blockchain interactions safer and easier.
- Multiple projects have begun testing implementations within testnets; some wallets now experiment with integrating abstracted account capabilities.
- Discussions continue around scalability concerns; critics worry about increased complexity potentially impacting network performance if not carefully managed.
Despite ongoing debates about potential scalability bottlenecks—which could arise from added computational overhead—the consensus remains optimistic about its long-term benefits when properly implemented.
Challenges Facing Implementation
While promising, adopting EIP-4337 involves navigating several hurdles:
Scalability Concerns
Adding sophisticated logic directly into accounts might increase transaction processing times or block sizes unless optimized effectively—a crucial consideration given Ethereum’s current throughput limits.
Regulatory Implications
Enhanced security features such as social recovery could raise questions around compliance with legal standards related to identity verification and anti-money laundering regulations across jurisdictions worldwide.
Adoption Timeline
Although initial testing phases began around 2022–2023—with some projects already integrating elements—the full rollout depends heavily on network upgrades (like Shanghai/Capella upgrades) scheduled over upcoming ETH network hard forks.
How Account Abstraction Shapes Future Blockchain Use Cases
If successfully implemented at scale:
- Users will enjoy simplified onboarding processes—no longer needing complex seed phrases managed manually.
- Developers will gain tools for building smarter dApps capable of handling multi-layered permissions natively within user accounts themselves.
- Security protocols will become more robust through customizable safeguards embedded directly into wallet logic rather than relying solely on external hardware solutions.
This evolution aligns well with broader trends toward decentralization combined with enhanced usability—a key factor driving mainstream adoption beyond crypto enthusiasts toward everyday consumers.
By reimagining how identities interact within blockchain ecosystems through proposals like EIP-4337—and addressing longstanding usability issues—it paves the way toward a future where decentralized finance becomes accessible yet secure enough for mass adoption. As ongoing developments unfold over 2024+, observing how communities adapt these innovations will be crucial in understanding their impact across various sectors—from finance institutions adopting blockchain-based identity solutions to individual users seeking safer ways to manage digital assets efficiently.


JCUSER-WVMdslBw
2025-05-14 12:53
What is account abstraction (EIP-4337)?
What is Account Abstraction (EIP-4337)?
Understanding Ethereum Accounts and Their Limitations
Ethereum, the leading blockchain platform for decentralized applications, has traditionally relied on two main types of accounts: externally owned accounts (EOAs) and contract accounts. EOAs are controlled by private keys and are used by users to send transactions, while contract accounts are governed by smart contracts that execute code autonomously. However, this binary structure presents certain limitations in terms of flexibility, security, and user experience.
For example, EOAs require users to manage private keys securely—an often complex task that can lead to loss of funds if mishandled. Contract accounts lack the ability to perform certain operations without external triggers or specific transaction structures. As Ethereum's ecosystem expands into areas like DeFi (Decentralized Finance), NFTs (Non-Fungible Tokens), and enterprise solutions, these constraints hinder seamless user interactions and advanced functionalities.
This context has driven the development of Account Abstraction, a concept aimed at redefining how Ethereum accounts function—making them more versatile and adaptable to modern needs.
What Is Account Abstraction?
Account abstraction refers to a paradigm shift in Ethereum's account model that allows for more flexible account behaviors beyond simple storage of Ether or tokens. Instead of being limited to basic transaction validation via private keys, abstracted accounts can incorporate custom logic for authorization, multi-signature schemes, social recovery mechanisms, or even biometric authentication.
Specifically related to EIP-4337—a prominent proposal within this space—it introduces a new layer where user operations are processed differently from traditional transactions. This enables users to execute complex actions without relying solely on externally owned wallets or traditional smart contracts as intermediaries.
In essence, account abstraction aims to make blockchain interactions more intuitive while enhancing security features such as multi-factor authentication or time-locks directly integrated into account logic.
The Context Behind EIP-4337 Development
The push towards account abstraction stems from several challenges faced by the Ethereum community:
User Experience: Managing private keys is cumbersome for many users; losing access means losing funds.
Security Risks: Private key management exposes vulnerabilities; compromised keys lead directly to asset theft.
Smart Contract Limitations: Existing models do not support advanced features like social recovery or flexible authorization schemes natively.
Scalability & Usability Needs: As DeFi grows exponentially with millions engaging in financial activities on-chain — there’s a pressing need for smarter account management systems that can handle complex workflows efficiently.
In response these issues have prompted proposals like EIP-4337 which aim at creating an improved framework where user operations can be processed more flexibly while maintaining compatibility with existing infrastructure.
Key Features of EIP-4337
Introduced in 2021 by members of the Ethereum community through extensive discussions and development efforts, EIP-4337 proposes several core innovations:
Abstract Accounts & Signers
The proposal introduces two primary components:
- Abstract Accounts: These are enhanced wallet-like entities capable of executing arbitrary transactions based on custom logic embedded within them.
- Abstract Signers: They facilitate signing transactions without exposing sensitive details—enabling features like multi-signature requirements seamlessly integrated into the account itself rather than relying solely on external wallets.
Improved Security Mechanisms
EIP-4337 emphasizes security enhancements such as:
- Multi-signature requirements ensuring multiple approvals before executing critical actions.
- Time-locks preventing immediate transfers—adding layers against unauthorized access.
- Social recovery options allowing trusted contacts or mechanisms restoring access if private keys are lost.
Compatibility & Transition
A significant aspect is backward compatibility with existing Ethereum infrastructure—meaning developers can adopt new features gradually without disrupting current applications or wallets during transition phases.
Recent Progress and Community Engagement
Since its proposal in 2021:
- The idea has gained substantial support among developers aiming at making blockchain interactions safer and easier.
- Multiple projects have begun testing implementations within testnets; some wallets now experiment with integrating abstracted account capabilities.
- Discussions continue around scalability concerns; critics worry about increased complexity potentially impacting network performance if not carefully managed.
Despite ongoing debates about potential scalability bottlenecks—which could arise from added computational overhead—the consensus remains optimistic about its long-term benefits when properly implemented.
Challenges Facing Implementation
While promising, adopting EIP-4337 involves navigating several hurdles:
Scalability Concerns
Adding sophisticated logic directly into accounts might increase transaction processing times or block sizes unless optimized effectively—a crucial consideration given Ethereum’s current throughput limits.
Regulatory Implications
Enhanced security features such as social recovery could raise questions around compliance with legal standards related to identity verification and anti-money laundering regulations across jurisdictions worldwide.
Adoption Timeline
Although initial testing phases began around 2022–2023—with some projects already integrating elements—the full rollout depends heavily on network upgrades (like Shanghai/Capella upgrades) scheduled over upcoming ETH network hard forks.
How Account Abstraction Shapes Future Blockchain Use Cases
If successfully implemented at scale:
- Users will enjoy simplified onboarding processes—no longer needing complex seed phrases managed manually.
- Developers will gain tools for building smarter dApps capable of handling multi-layered permissions natively within user accounts themselves.
- Security protocols will become more robust through customizable safeguards embedded directly into wallet logic rather than relying solely on external hardware solutions.
This evolution aligns well with broader trends toward decentralization combined with enhanced usability—a key factor driving mainstream adoption beyond crypto enthusiasts toward everyday consumers.
By reimagining how identities interact within blockchain ecosystems through proposals like EIP-4337—and addressing longstanding usability issues—it paves the way toward a future where decentralized finance becomes accessible yet secure enough for mass adoption. As ongoing developments unfold over 2024+, observing how communities adapt these innovations will be crucial in understanding their impact across various sectors—from finance institutions adopting blockchain-based identity solutions to individual users seeking safer ways to manage digital assets efficiently.
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
Fundstrat's Tom Lee, the strategist who correctly called Bitcoin's 2017 surge, has made his boldest prediction yet: Ethereum could hit $15,000 by year-end 2025. His conviction is backed by BitMine Immersion Technologies' record-breaking $5 billion ETH treasury accumulation.
💰 The Bold Investment Thesis:
-
Price Target: $4K by July, $10K-$15K by year-end 2025 (400% upside potential)
Corporate Treasury: 1.15 million ETH ($5B) - world's largest corporate Ethereum position
Growth Strategy: Targeting 5% of total ETH supply (~6 million tokens worth $25B+)
Market Driver: Stablecoin explosion from $250B to $2T market cap
🎯 Key Catalysts Driving the Prediction:
1️⃣ Stablecoin Dominance: Ethereum powers 60%+ of all stablecoin transactions - the "ChatGPT moment" for crypto adoption 2️⃣ Wall Street's Choice: Institutions prefer Ethereum for regulatory compliance and established infrastructure 3️⃣ Real-World Assets: 60% market share in asset tokenization as traditional finance goes digital 4️⃣ Treasury Strategy: BitMine accumulating ETH 12x faster than MicroStrategy's Bitcoin pace
🏆 BitMine's Aggressive Accumulation:
-
Holdings: 1.15M ETH worth ~$5B (targeting 5% of total supply)
Stock Performance: BMNR up 634% year-to-date
Trading Volume: $1.6B daily, rivaling major corporations
Expansion: $24.5B equity offering for additional acquisitions
Staking Rewards: Earning ~3% annual yields on ETH holdings
💡 The "Digital Infrastructure" Thesis:
Why ETH > BTC for Institutions:
-
Bitcoin = Digital Gold (store of value)
Ethereum = Financial Infrastructure (powers the digital economy)
Stablecoins creating viral adoption among banks, merchants, consumers
JPMorgan, Visa, Robinhood building on Ethereum infrastructure
🔥 Technical Analysis & Targets:
-
Immediate: $4,000 breakout level (July 2025)
Historical Ratio: ETH/BTC returning to 2017 peak suggests $16,000 potential
Fundamental Value: Circle's 100x EBITDA multiple applied to Ethereum = $10K+ fair value
Network Effects: 10-year operational history without downtime = institutional confidence
📊 Market Transformation Indicators:
-
Stablecoin Growth: 8x expansion potential ($250B → $2T)
Fee Revenue: 10x network fee growth from increased usage
Regulatory Support: GENIUS Act providing legal framework
Corporate Adoption: Treasury strategies becoming mainstream
⚠️ Investment Considerations:
Opportunities:
-
Leveraged exposure through BitMine stock (BMNR)
Direct ETH investment at potentially attractive entry points
1-2% portfolio allocation recommended for conservative investors
Risks:
-
Blockchain competition (Solana, others offering faster/cheaper alternatives)
Regulatory uncertainties around stablecoins
Market volatility (30-50% drawdowns possible)
Layer 2 scaling potentially reducing Layer 1 value capture
💎 Bottom Line:
Tom Lee's $15K Ethereum prediction isn't just price speculation—it's a thesis about Ethereum becoming the backbone of digitized traditional finance. With BitMine's $5B bet and stablecoin adoption accelerating, Ethereum could experience its "Bitcoin 2017 moment" driven by institutional adoption rather than retail speculation.
The strategy mirrors MicroStrategy's Bitcoin approach but focuses on Ethereum's unique utility in powering the next generation of financial infrastructure. Success depends on continued stablecoin growth and real-world asset tokenization dominance.
Read the complete analysis and investment strategy breakdown: 👇 https://blog.jucoin.com/tom-lee-ethereum-prediction/
#Ethereum #TomLee #BitMine


JU Blog
2025-08-13 07:50
🚀 Wall Street Legend Tom Lee Predicts Ethereum $15K by 2025 with $5B Corporate Bet!
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
What Is Proof-of-Stake (PoS)?
Proof-of-Stake (PoS) is a consensus mechanism used in blockchain technology to validate transactions and secure the network. Unlike the traditional Proof-of-Work (PoW), which relies on miners solving complex mathematical puzzles through energy-intensive computations, PoS selects validators based on the amount of cryptocurrency they "stake" or lock up as collateral. This approach aims to create a more efficient, scalable, and environmentally friendly way of maintaining blockchain integrity.
How Does Proof-of-Stake Work?
In a PoS system, participants known as validators are chosen to create new blocks based on their stake in the network. The more coins a validator commits, the higher their chances of being selected to validate transactions and add new blocks to the chain. This process involves several key steps:
- Staking: Validators lock up a specific amount of cryptocurrency as collateral.
- Validator Selection: The network randomly or deterministically selects validators based on factors like stake size and sometimes other criteria such as coin age.
- Validation: Selected validators verify transactions within proposed blocks.
- Reward & Penalties: Successful validation earns rewards; misbehavior results in penalties like slashing—where part or all of their staked coins are forfeited.
This method ensures that those with more at stake have greater incentive to act honestly since malicious activity can lead to significant financial loss.
Advantages of Proof-of-Stake
Proof-of-Stake offers several benefits over traditional PoW systems:
Energy Efficiency
One of PoS's most significant advantages is its lower energy consumption. Since it eliminates the need for computationally intensive mining operations, it reduces electricity usage drastically—making blockchain networks more sustainable and environmentally friendly.
Scalability
PoS allows for faster transaction processing times and higher throughput compared to PoW networks. This scalability makes it suitable for applications requiring high-speed data validation without compromising security.
Security Features
While no system is entirely immune from attacks, well-designed PoS protocols incorporate mechanisms like slashing penalties that discourage malicious behavior. Additionally, because validators risk losing their staked assets if they act dishonestly, this creates economic incentives aligned with honest participation.
Challenges & Risks Associated With Proof-of-Stake
Despite its advantages, PoS faces certain challenges that developers and stakeholders must address:
Nothing-at-Stake Problem
In some early implementations of PoS, validators could vote for multiple conflicting chains without penalty—a situation called "nothing-at-stake." To mitigate this risk, modern protocols implement slashing conditions where misbehavior leads to penalties severe enough to deter such actions.
Centralization Concerns
Since larger stakeholders have increased influence over block creation probabilities, there's potential for wealth concentration leading to centralization risks—where power becomes concentrated among few large holders rather than distributed evenly across participants.
Security Considerations
Although generally considered secure when properly implemented, emerging attack vectors specific to staking systems require ongoing research and protocol improvements. Continuous updates help maintain resilience against threats like long-range attacks or validator collusion.
Ethereum’s Transition From Proof-of-Work To Proof-of-Stake
Ethereum’s move from proof-of-work (PoW) toward proof-of-stake (PoS) represents one of the most prominent real-world applications demonstrating this consensus mechanism's potential. Launched initially in December 2020 via its Beacon Chain upgrade—the first phase towards Ethereum 2.0—the transition aimed at addressing scalability issues while significantly reducing energy consumption associated with mining activities.
The milestone event called "The Merge," completed in 2023 after years of development effort by Ethereum developers worldwide—including extensive testing—marked Ethereum’s full switch from energy-intensive mining toward an eco-friendly staking model. This shift not only enhances sustainability but also paves the way for future upgrades focused on increasing transaction throughput through sharding techniques integrated into Eth2 architecture.
Future Outlook & Adoption Trends
As major cryptocurrencies adopt proof-of-stake mechanisms—including Cardano (ADA), Solana (SOL), Polkadot (DOT), among others—the landscape is witnessing rapid growth driven by both technological advancements and environmental considerations. Stakeholder interest continues rising due primarily to benefits like reduced operational costs and improved scalability prospects which appeal both investors seeking returns via staking rewards—and developers aiming for robust decentralized applications capable of handling mass adoption scenarios efficiently.
However, widespread adoption also brings regulatory scrutiny; authorities worldwide are beginning scrutinizing staking practices concerning investor protections and compliance frameworks—a factor that could influence future development directions within this space significantly.
Key Takeaways About Proof-of-Stake
To summarize what makes proof-of-stake distinct:
- Validators participate by locking up tokens instead of performing resource-heavy computations.
- It offers superior energy efficiency compared with proof-of-work.
- Security relies heavily on economic incentives; misbehavior results in financial penalties.
- Major networks like Ethereum have successfully transitioned or plan transitions towards PoS models.
Understanding these core aspects helps users evaluate whether adopting or supporting proof-based blockchain projects aligns with their goals—whether it's investing safely or developing scalable decentralized solutions.
Addressing User Concerns & Trustworthiness
For users considering involvement in staking activities—or simply wanting clarity about how these systems operate—it’s crucial first understanding security measures involved such as slashing conditions designed specifically against malicious actions—and how decentralization efforts aim at preventing undue influence by large stakeholders alone.
Furthermore,
- Look into reputable platforms offering staking services,
- Review governance structures ensuring transparency,
- Stay updated about ongoing protocol improvements addressing vulnerabilities,
are essential steps toward engaging confidently within evolving proof-based ecosystems.
Final Thoughts
Proof-of-stake has emerged as an innovative alternative that addresses many limitations inherent in traditional blockchain consensus mechanisms while promoting sustainability through reduced energy use—and fostering scalability necessary for mainstream adoption today’s digital economy demands increasingly efficient infrastructure solutions rooted firmly in trustworthiness backed by transparent governance models.


JCUSER-WVMdslBw
2025-05-11 10:39
What is proof-of-stake?
What Is Proof-of-Stake (PoS)?
Proof-of-Stake (PoS) is a consensus mechanism used in blockchain technology to validate transactions and secure the network. Unlike the traditional Proof-of-Work (PoW), which relies on miners solving complex mathematical puzzles through energy-intensive computations, PoS selects validators based on the amount of cryptocurrency they "stake" or lock up as collateral. This approach aims to create a more efficient, scalable, and environmentally friendly way of maintaining blockchain integrity.
How Does Proof-of-Stake Work?
In a PoS system, participants known as validators are chosen to create new blocks based on their stake in the network. The more coins a validator commits, the higher their chances of being selected to validate transactions and add new blocks to the chain. This process involves several key steps:
- Staking: Validators lock up a specific amount of cryptocurrency as collateral.
- Validator Selection: The network randomly or deterministically selects validators based on factors like stake size and sometimes other criteria such as coin age.
- Validation: Selected validators verify transactions within proposed blocks.
- Reward & Penalties: Successful validation earns rewards; misbehavior results in penalties like slashing—where part or all of their staked coins are forfeited.
This method ensures that those with more at stake have greater incentive to act honestly since malicious activity can lead to significant financial loss.
Advantages of Proof-of-Stake
Proof-of-Stake offers several benefits over traditional PoW systems:
Energy Efficiency
One of PoS's most significant advantages is its lower energy consumption. Since it eliminates the need for computationally intensive mining operations, it reduces electricity usage drastically—making blockchain networks more sustainable and environmentally friendly.
Scalability
PoS allows for faster transaction processing times and higher throughput compared to PoW networks. This scalability makes it suitable for applications requiring high-speed data validation without compromising security.
Security Features
While no system is entirely immune from attacks, well-designed PoS protocols incorporate mechanisms like slashing penalties that discourage malicious behavior. Additionally, because validators risk losing their staked assets if they act dishonestly, this creates economic incentives aligned with honest participation.
Challenges & Risks Associated With Proof-of-Stake
Despite its advantages, PoS faces certain challenges that developers and stakeholders must address:
Nothing-at-Stake Problem
In some early implementations of PoS, validators could vote for multiple conflicting chains without penalty—a situation called "nothing-at-stake." To mitigate this risk, modern protocols implement slashing conditions where misbehavior leads to penalties severe enough to deter such actions.
Centralization Concerns
Since larger stakeholders have increased influence over block creation probabilities, there's potential for wealth concentration leading to centralization risks—where power becomes concentrated among few large holders rather than distributed evenly across participants.
Security Considerations
Although generally considered secure when properly implemented, emerging attack vectors specific to staking systems require ongoing research and protocol improvements. Continuous updates help maintain resilience against threats like long-range attacks or validator collusion.
Ethereum’s Transition From Proof-of-Work To Proof-of-Stake
Ethereum’s move from proof-of-work (PoW) toward proof-of-stake (PoS) represents one of the most prominent real-world applications demonstrating this consensus mechanism's potential. Launched initially in December 2020 via its Beacon Chain upgrade—the first phase towards Ethereum 2.0—the transition aimed at addressing scalability issues while significantly reducing energy consumption associated with mining activities.
The milestone event called "The Merge," completed in 2023 after years of development effort by Ethereum developers worldwide—including extensive testing—marked Ethereum’s full switch from energy-intensive mining toward an eco-friendly staking model. This shift not only enhances sustainability but also paves the way for future upgrades focused on increasing transaction throughput through sharding techniques integrated into Eth2 architecture.
Future Outlook & Adoption Trends
As major cryptocurrencies adopt proof-of-stake mechanisms—including Cardano (ADA), Solana (SOL), Polkadot (DOT), among others—the landscape is witnessing rapid growth driven by both technological advancements and environmental considerations. Stakeholder interest continues rising due primarily to benefits like reduced operational costs and improved scalability prospects which appeal both investors seeking returns via staking rewards—and developers aiming for robust decentralized applications capable of handling mass adoption scenarios efficiently.
However, widespread adoption also brings regulatory scrutiny; authorities worldwide are beginning scrutinizing staking practices concerning investor protections and compliance frameworks—a factor that could influence future development directions within this space significantly.
Key Takeaways About Proof-of-Stake
To summarize what makes proof-of-stake distinct:
- Validators participate by locking up tokens instead of performing resource-heavy computations.
- It offers superior energy efficiency compared with proof-of-work.
- Security relies heavily on economic incentives; misbehavior results in financial penalties.
- Major networks like Ethereum have successfully transitioned or plan transitions towards PoS models.
Understanding these core aspects helps users evaluate whether adopting or supporting proof-based blockchain projects aligns with their goals—whether it's investing safely or developing scalable decentralized solutions.
Addressing User Concerns & Trustworthiness
For users considering involvement in staking activities—or simply wanting clarity about how these systems operate—it’s crucial first understanding security measures involved such as slashing conditions designed specifically against malicious actions—and how decentralization efforts aim at preventing undue influence by large stakeholders alone.
Furthermore,
- Look into reputable platforms offering staking services,
- Review governance structures ensuring transparency,
- Stay updated about ongoing protocol improvements addressing vulnerabilities,
are essential steps toward engaging confidently within evolving proof-based ecosystems.
Final Thoughts
Proof-of-stake has emerged as an innovative alternative that addresses many limitations inherent in traditional blockchain consensus mechanisms while promoting sustainability through reduced energy use—and fostering scalability necessary for mainstream adoption today’s digital economy demands increasingly efficient infrastructure solutions rooted firmly in trustworthiness backed by transparent governance models.
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
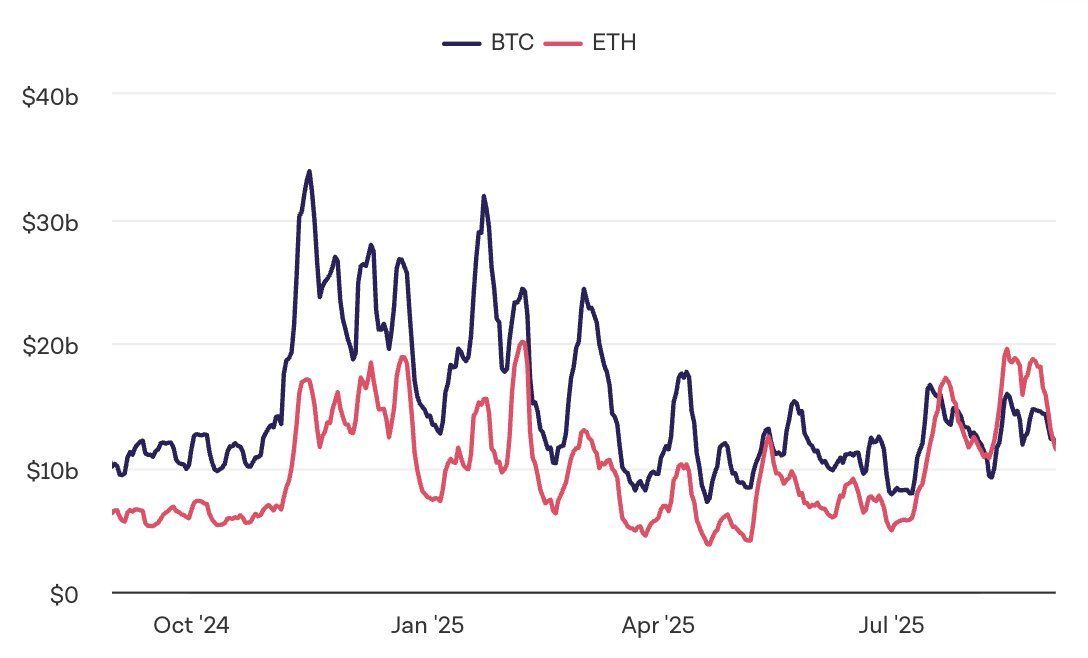
For the first time in 7 years, $ETH > $BTC in 7-day spot volume, per The Block. 🔁 👉 Bitcoin whales are rotating heavily into Ethereum.
With capital reallocating + rate cut anticipation, analysts now eye fresh ATHs in Q4 for majors.
#Ethereum #Bitcoin #cryptocurrency #blockchain


Carmelita
2025-09-04 16:37
🚨 Historic Shift on CEXs
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
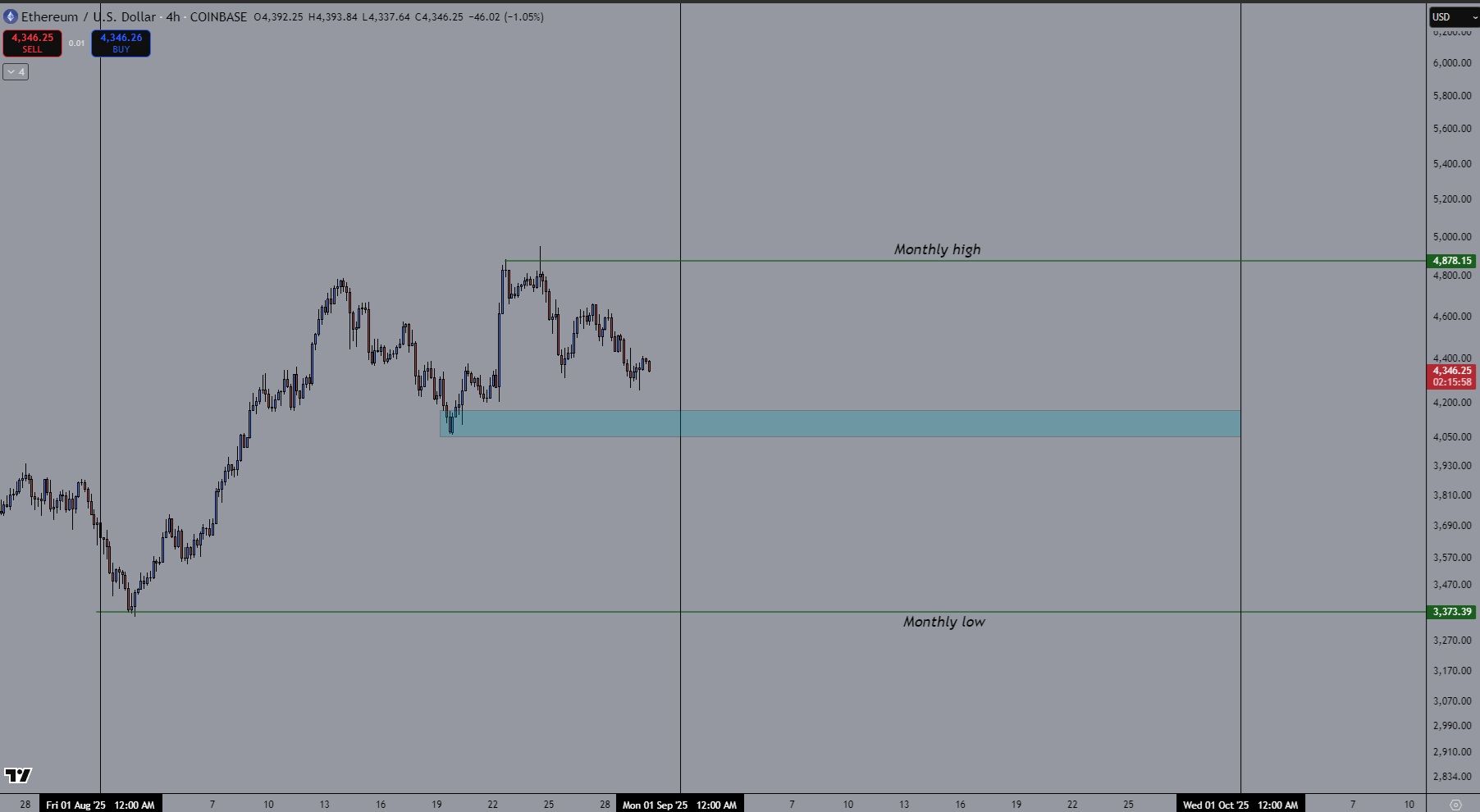
Début de mois = possible dip 📉 2ᵉ moitié = éventuelle étincelle si la Fed coupe les taux 🔥
👉 Septembre pourrait être le mois pour se positionner avant le prochain leg haussier. 🚀
#Ethereum #crypto


Carmelita
2025-08-30 23:40
$ETH – Septembre en ligne de mire
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
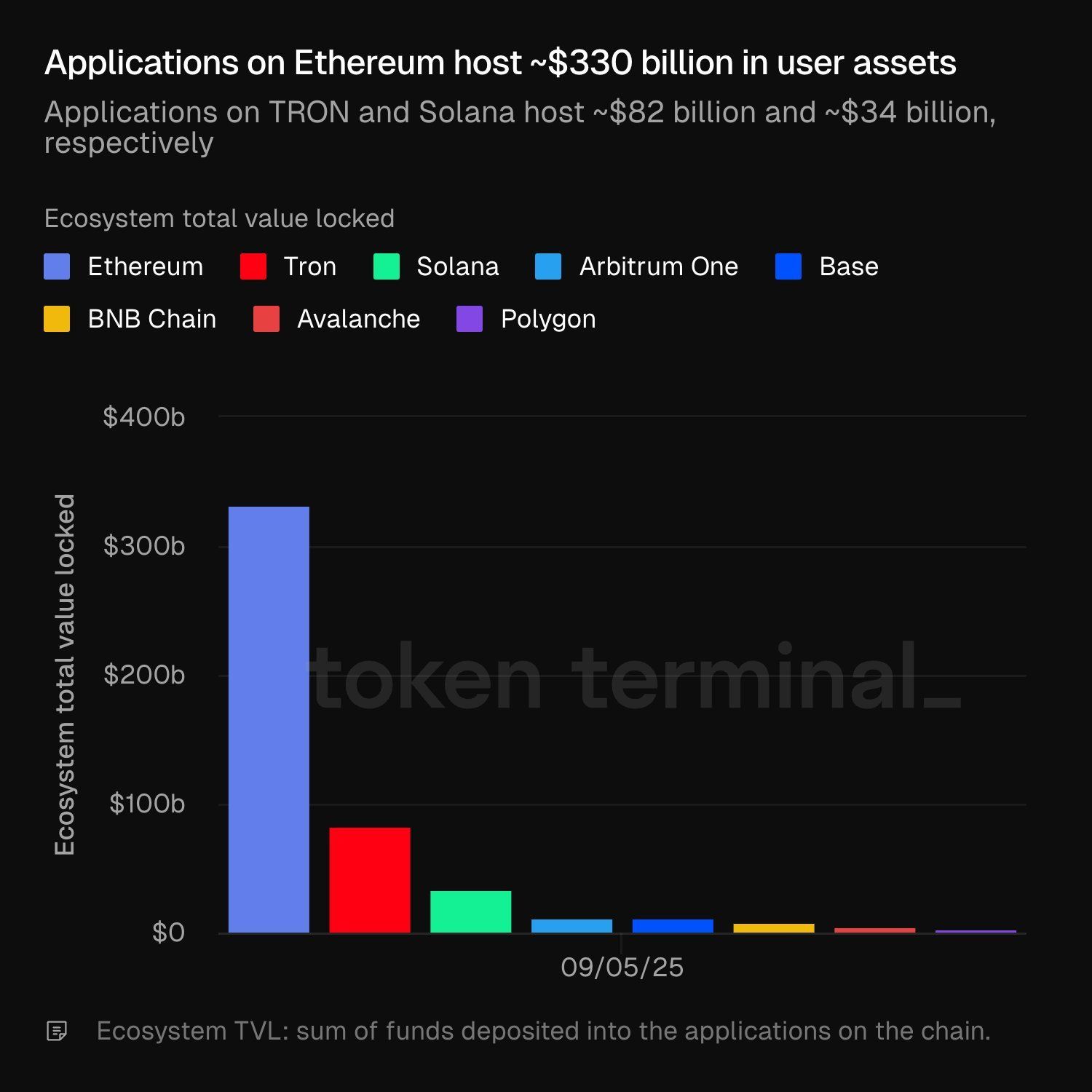
$TRX/USDT : ~$82B |$SOL/USDT : ~$34B
Le TVL des écosystèmes révèle où le vrai capital circule. Suivez les flux et soyez prêts pour la prochaine opportunité. 👀
#Ethereum #CryptoInsights #cryptocurrency #blockchain


Carmelita
2025-09-06 16:53
🔥 Ethereum domine le game !
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
➡️ Achat de 2,588 $BTC/USDT pour 258,8 M$ 🟢 ➡️ Vente de 35,009 $ETH/USDT pour 152,7 M$ 🔴
Un rééquilibrage massif qui en dit long sur leur vision court-terme du marché. 👀
#Bitcoin #Ethereum #cryptocurrency #blockchain



Carmelita
2025-09-04 13:11
🔥 Mouvement stratégique de BlackRock aujourd’hui
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
How Has the Net Staking Participation Rate Evolved on Ethereum Since the Merge?
Understanding Ethereum’s Transition to Proof of Stake
Ethereum's transition from proof-of-work (PoW) to proof-of-stake (PoS), known as "The Merge," took place on September 15, 2022. This significant upgrade aimed to enhance the network’s scalability, security, and energy efficiency. Unlike PoW, which relies on miners solving complex puzzles to validate transactions, PoS depends on validators who stake their ETH tokens to participate in consensus. This shift was driven by a desire to reduce energy consumption and improve network sustainability while maintaining decentralization.
Initial Impact of The Merge on Validator Participation
Immediately following The Merge, there was a notable surge in validator activity. Many users and institutions saw staking as an attractive opportunity due to the potential for earning rewards through newly minted ETH. This initial enthusiasm led to a rapid increase in active validators—participants actively involved in validating transactions and securing the network.
This spike reflected both market optimism and confidence in Ethereum’s new consensus mechanism. Validators were incentivized not only by staking rewards but also by supporting a more sustainable blockchain infrastructure. During this period, participation rates reached high levels compared with pre-Merge figures.
Trends in Validator Growth Post-Merge
Since that initial surge, data indicates that while validator participation has stabilized somewhat, there has been consistent growth in total validator numbers over time. The number of active validators tends to fluctuate based on market conditions but generally shows an upward trend.
This steady increase suggests ongoing interest from individual investors and institutional players alike who recognize staking as a long-term opportunity within Ethereum's ecosystem. As more ETH is staked—either directly or via third-party services—the overall security of the network continues improving due to increased decentralization efforts.
Factors Influencing Staking Participation Rates
Several key factors influence how many validators participate actively:
Market Volatility: Cryptocurrency markets are inherently volatile; during downturns or periods of high fluctuation, some validators may choose temporarily or permanently exit their positions either for risk mitigation or profit-taking.
Staking Rewards: The attractiveness of staking rewards plays a crucial role; higher yields tend to encourage more participation while reductions can lead some participants to withdraw.
Regulatory Environment: Legal clarity around crypto assets impacts validator engagement significantly. Favorable regulations can boost confidence among participants; uncertainty may cause hesitation or withdrawal.
Network Security Measures: Protocol upgrades like Casper FFG aim at preventing centralization risks by incentivizing diverse validator participation across different entities.
Challenges: Centralization Risks & Economic Incentives
While increased validator numbers are positive for decentralization and security, there's always concern about centralization—where control over large portions of staked ETH could threaten network integrity. If too few entities hold significant stakes (a phenomenon called "rich-get-richer"), it could undermine Ethereum's decentralized ethos despite technical safeguards like Casper FFG designed for fairness.
Economic incentives remain vital: if staking rewards diminish due to protocol changes or market conditions such as declining ETH prices relative to fiat currencies, fewer users might find validation profitable enough—potentially reducing overall participation rates over time.
Market Volatility’s Effect on Validator Engagement
The cryptocurrency landscape is highly sensitive; sharp price swings often impact user behavior regarding staking activities:
- During bullish phases with rising ETH prices and strong market sentiment, more users are motivated by potential gains.
- Conversely, during bearish trends or high volatility episodes—such as sudden dips—they might withdraw their stakes temporarily or entirely exit until conditions stabilize.
Such fluctuations can cause short-term dips but typically do not significantly alter long-term growth trends if underlying fundamentals remain strong.
Regulatory Developments Shaping Future Participation
Regulatory clarity remains one of the most influential external factors affecting net staking rates post-Merge:
- Countries like the United States have begun clarifying rules around crypto assets which tend toward encouraging institutional involvement.
- Conversely, regulatory crackdowns or ambiguous policies could deter smaller investors from participating further into staking activities due to compliance concerns or legal uncertainties.
As governments worldwide refine their stance towards cryptocurrencies—including proposals related specifically to securities classification—the future landscape for Ethereum validators will be shaped accordingly.
Maintaining Decentralization & Economic Incentives for Sustained Growth
Ensuring that validation remains decentralized requires continuous efforts beyond just increasing numbers:
- Protocol updates should promote fair distribution among diverse participants.
- Reward structures must balance profitability with inclusivity so smaller holders can participate without disproportionate influence.
- Education campaigns can help new users understand benefits and risks associated with staking under evolving regulatory environments.
Tracking Long-Term Trends: Is Validator Participation Sustainable?
Overall data suggests that since The Merge,
- Validator counts have grown steadily,
- Initial enthusiasm has transitioned into sustained interest,
- Fluctuations driven by market dynamics are normal but do not threaten overall upward momentum,
indicating robust confidence within parts of the community about Ethereum’s future prospects under PoS governance.
Final Thoughts: What Does It Mean for Users & Investors?
For existing stakeholders considering whether they should stake their ETH—or newcomers evaluating entry points—the evolving net participation rate offers valuable insights into network health:
- A high level indicates strong community engagement,
- Growing validator numbers suggest increasing trust,
- Stability amidst volatility reflects resilience,
making it clear that despite challenges posed by external factors like regulation and market swings—all signs point toward continued maturation of Ethereum's proof-of-stake ecosystem.
References


Lo
2025-05-11 06:24
How has the net staking participation rate evolved on Ethereum (ETH) since the Merge?
How Has the Net Staking Participation Rate Evolved on Ethereum Since the Merge?
Understanding Ethereum’s Transition to Proof of Stake
Ethereum's transition from proof-of-work (PoW) to proof-of-stake (PoS), known as "The Merge," took place on September 15, 2022. This significant upgrade aimed to enhance the network’s scalability, security, and energy efficiency. Unlike PoW, which relies on miners solving complex puzzles to validate transactions, PoS depends on validators who stake their ETH tokens to participate in consensus. This shift was driven by a desire to reduce energy consumption and improve network sustainability while maintaining decentralization.
Initial Impact of The Merge on Validator Participation
Immediately following The Merge, there was a notable surge in validator activity. Many users and institutions saw staking as an attractive opportunity due to the potential for earning rewards through newly minted ETH. This initial enthusiasm led to a rapid increase in active validators—participants actively involved in validating transactions and securing the network.
This spike reflected both market optimism and confidence in Ethereum’s new consensus mechanism. Validators were incentivized not only by staking rewards but also by supporting a more sustainable blockchain infrastructure. During this period, participation rates reached high levels compared with pre-Merge figures.
Trends in Validator Growth Post-Merge
Since that initial surge, data indicates that while validator participation has stabilized somewhat, there has been consistent growth in total validator numbers over time. The number of active validators tends to fluctuate based on market conditions but generally shows an upward trend.
This steady increase suggests ongoing interest from individual investors and institutional players alike who recognize staking as a long-term opportunity within Ethereum's ecosystem. As more ETH is staked—either directly or via third-party services—the overall security of the network continues improving due to increased decentralization efforts.
Factors Influencing Staking Participation Rates
Several key factors influence how many validators participate actively:
Market Volatility: Cryptocurrency markets are inherently volatile; during downturns or periods of high fluctuation, some validators may choose temporarily or permanently exit their positions either for risk mitigation or profit-taking.
Staking Rewards: The attractiveness of staking rewards plays a crucial role; higher yields tend to encourage more participation while reductions can lead some participants to withdraw.
Regulatory Environment: Legal clarity around crypto assets impacts validator engagement significantly. Favorable regulations can boost confidence among participants; uncertainty may cause hesitation or withdrawal.
Network Security Measures: Protocol upgrades like Casper FFG aim at preventing centralization risks by incentivizing diverse validator participation across different entities.
Challenges: Centralization Risks & Economic Incentives
While increased validator numbers are positive for decentralization and security, there's always concern about centralization—where control over large portions of staked ETH could threaten network integrity. If too few entities hold significant stakes (a phenomenon called "rich-get-richer"), it could undermine Ethereum's decentralized ethos despite technical safeguards like Casper FFG designed for fairness.
Economic incentives remain vital: if staking rewards diminish due to protocol changes or market conditions such as declining ETH prices relative to fiat currencies, fewer users might find validation profitable enough—potentially reducing overall participation rates over time.
Market Volatility’s Effect on Validator Engagement
The cryptocurrency landscape is highly sensitive; sharp price swings often impact user behavior regarding staking activities:
- During bullish phases with rising ETH prices and strong market sentiment, more users are motivated by potential gains.
- Conversely, during bearish trends or high volatility episodes—such as sudden dips—they might withdraw their stakes temporarily or entirely exit until conditions stabilize.
Such fluctuations can cause short-term dips but typically do not significantly alter long-term growth trends if underlying fundamentals remain strong.
Regulatory Developments Shaping Future Participation
Regulatory clarity remains one of the most influential external factors affecting net staking rates post-Merge:
- Countries like the United States have begun clarifying rules around crypto assets which tend toward encouraging institutional involvement.
- Conversely, regulatory crackdowns or ambiguous policies could deter smaller investors from participating further into staking activities due to compliance concerns or legal uncertainties.
As governments worldwide refine their stance towards cryptocurrencies—including proposals related specifically to securities classification—the future landscape for Ethereum validators will be shaped accordingly.
Maintaining Decentralization & Economic Incentives for Sustained Growth
Ensuring that validation remains decentralized requires continuous efforts beyond just increasing numbers:
- Protocol updates should promote fair distribution among diverse participants.
- Reward structures must balance profitability with inclusivity so smaller holders can participate without disproportionate influence.
- Education campaigns can help new users understand benefits and risks associated with staking under evolving regulatory environments.
Tracking Long-Term Trends: Is Validator Participation Sustainable?
Overall data suggests that since The Merge,
- Validator counts have grown steadily,
- Initial enthusiasm has transitioned into sustained interest,
- Fluctuations driven by market dynamics are normal but do not threaten overall upward momentum,
indicating robust confidence within parts of the community about Ethereum’s future prospects under PoS governance.
Final Thoughts: What Does It Mean for Users & Investors?
For existing stakeholders considering whether they should stake their ETH—or newcomers evaluating entry points—the evolving net participation rate offers valuable insights into network health:
- A high level indicates strong community engagement,
- Growing validator numbers suggest increasing trust,
- Stability amidst volatility reflects resilience,
making it clear that despite challenges posed by external factors like regulation and market swings—all signs point toward continued maturation of Ethereum's proof-of-stake ecosystem.
References
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
How the Beacon Chain Coordinates Validator Duties and Shard Transitions in Ethereum
Understanding how Ethereum's Beacon Chain manages validator responsibilities and facilitates shard transitions is essential for grasping the network’s ongoing evolution toward scalability and security. As part of Ethereum 2.0, the Beacon Chain introduces a new proof-of-stake (PoS) consensus mechanism that replaces traditional proof-of-work (PoW). This shift aims to make the network more sustainable, efficient, and capable of handling increased transaction volumes through sharding.
The Role of the Beacon Chain in Validator Coordination
The Beacon Chain acts as the backbone for validator management within Ethereum 2.0. Validators are responsible for proposing new blocks, validating transactions, and maintaining network security. Unlike miners in PoW systems, validators are chosen based on their staked ETH—meaning their financial commitment directly influences their chances of participating in block creation.
Validator selection is governed by a randomized process that ensures fairness while incentivizing honest participation. When selected to propose a block during a specific slot—a fixed time interval—the validator must create or validate transactions within that window. To prevent malicious activities such as double proposals or equivocation, Ethereum employs slashing mechanisms: if validators act dishonestly or fail to perform duties correctly, they risk losing part or all of their staked ETH.
The Beacon Chain organizes these activities into epochs—larger time frames composed of multiple slots (typically 32). Each epoch allows for validator rotations and updates to be processed systematically, ensuring smooth operation across the entire network.
Managing Shard Transitions for Scalability
One of Ethereum 2.0’s primary goals is scalability through sharding—a technique where the blockchain is split into smaller pieces called shards that operate concurrently. Each shard handles its own subset of transactions and smart contracts, significantly increasing overall throughput compared to a single monolithic chain.
Shard transitions involve several key steps:
- Initialization: The Beacon Chain assigns validators to different shards based on current network needs.
- Activation Phases: Shards are gradually activated through phased rollouts—initially testing shard functionality via dedicated testnets like the Shard Canary Network launched in 2023.
- Data Migration: During transition phases, data from existing chains migrates into shards seamlessly without disrupting ongoing operations.
- Cross-Linking Mechanisms: To enable communication between shards—such as transferring assets or verifying cross-shard data—the protocol implements cross-linking structures that connect individual shard chains back to the main chain.
This architecture allows multiple transactions across different shards simultaneously without bottlenecking at one point—a significant improvement over traditional blockchain models prone to congestion during high demand periods.
Recent Developments Supporting Validator Coordination & Sharding
Ethereum's recent advancements underscore its commitment toward achieving full scalability with robust security measures:
Shard Canary Network (SCN): Launched in 2023 as an experimental environment for testing shard functionalities under real-world conditions before deploying on mainnet.
Mainnet Merge: Expected late 2023 or early 2024 marks a pivotal milestone where Ethereum will combine its existing PoW mainnet with the PoS-based Beacon Chain—a process known as "the Merge." This event will fully transition validation duties onto PoS while integrating sharding features progressively afterward.
These developments demonstrate continuous progress towards decentralization and efficiency but also highlight technical challenges such as ensuring secure cross-shard communication and maintaining validator incentives throughout complex upgrades.
Challenges Facing Validator Coordination & Shard Transition
While promising, transitioning from traditional blockchain architectures involves notable hurdles:
Technical Complexity: Implementing seamless communication between numerous shards requires sophisticated protocols; any vulnerabilities could compromise security.
Validator Participation Rates: The success hinges on active validator engagement; low participation could slow down progress or cause instability.
Network Security Risks: As complexity increases with sharding—and especially during transitional phases—the attack surface expands if not properly managed.
Regulatory Uncertainty: Evolving legal frameworks around cryptocurrencies may influence adoption rates among validators and users alike.
Addressing these issues demands rigorous testing—including testnets like SCN—and community support aligned with long-term development goals.
Key Facts About Ethereum’s Transition Timeline
| Event | Date/Expected Timeline | Significance |
|---|---|---|
| Launch of Beacon Chain | December 2020 | Foundation layer supporting staking |
| Launch of Shard Canary Network | 2023 | Testing environment for shard functionality |
| Expected Mainnet Merge | Late 2023 / Early 2024 | Full transition from PoW to PoS |
As these milestones approach, stakeholders closely monitor progress due to their impact on scalability improvements and overall network health.
Monitoring Future Developments in Validator Management & Sharding
Ethereum’s journey towards full-scale adoption relies heavily on effective coordination mechanisms provided by its consensus layer—the Beacon Chain—and successful implementation of sharding technology. Continuous upgrades aim not only at increasing transaction capacity but also at reinforcing decentralization by enabling more participants worldwide to become validators securely.
Staying informed about upcoming updates like protocol upgrades or testnet launches helps users understand how these changes might influence transaction speeds, costs (gas fees), security assurances, and overall user experience within this rapidly evolving ecosystem.
Final Thoughts: Navigating Growth Through Innovation
Ethereum's innovative approach via its beacon chain architecture exemplifies how layered coordination can transform blockchain networks into scalable platforms capable of supporting global applications—from decentralized finance (DeFi) projects to enterprise solutions—all while maintaining high-security standards through proof-of-stake validation processes combined with advanced sharding techniques.
By understanding how validator duties are managed alongside complex shard transitions—and keeping an eye on upcoming milestones—you can better appreciate both current capabilities and future potentialities shaping one of today’s most influential blockchain ecosystems


JCUSER-F1IIaxXA
2025-05-11 06:19
How does the Beacon Chain coordinate validator duties and shard transitions in Ethereum (ETH)?
How the Beacon Chain Coordinates Validator Duties and Shard Transitions in Ethereum
Understanding how Ethereum's Beacon Chain manages validator responsibilities and facilitates shard transitions is essential for grasping the network’s ongoing evolution toward scalability and security. As part of Ethereum 2.0, the Beacon Chain introduces a new proof-of-stake (PoS) consensus mechanism that replaces traditional proof-of-work (PoW). This shift aims to make the network more sustainable, efficient, and capable of handling increased transaction volumes through sharding.
The Role of the Beacon Chain in Validator Coordination
The Beacon Chain acts as the backbone for validator management within Ethereum 2.0. Validators are responsible for proposing new blocks, validating transactions, and maintaining network security. Unlike miners in PoW systems, validators are chosen based on their staked ETH—meaning their financial commitment directly influences their chances of participating in block creation.
Validator selection is governed by a randomized process that ensures fairness while incentivizing honest participation. When selected to propose a block during a specific slot—a fixed time interval—the validator must create or validate transactions within that window. To prevent malicious activities such as double proposals or equivocation, Ethereum employs slashing mechanisms: if validators act dishonestly or fail to perform duties correctly, they risk losing part or all of their staked ETH.
The Beacon Chain organizes these activities into epochs—larger time frames composed of multiple slots (typically 32). Each epoch allows for validator rotations and updates to be processed systematically, ensuring smooth operation across the entire network.
Managing Shard Transitions for Scalability
One of Ethereum 2.0’s primary goals is scalability through sharding—a technique where the blockchain is split into smaller pieces called shards that operate concurrently. Each shard handles its own subset of transactions and smart contracts, significantly increasing overall throughput compared to a single monolithic chain.
Shard transitions involve several key steps:
- Initialization: The Beacon Chain assigns validators to different shards based on current network needs.
- Activation Phases: Shards are gradually activated through phased rollouts—initially testing shard functionality via dedicated testnets like the Shard Canary Network launched in 2023.
- Data Migration: During transition phases, data from existing chains migrates into shards seamlessly without disrupting ongoing operations.
- Cross-Linking Mechanisms: To enable communication between shards—such as transferring assets or verifying cross-shard data—the protocol implements cross-linking structures that connect individual shard chains back to the main chain.
This architecture allows multiple transactions across different shards simultaneously without bottlenecking at one point—a significant improvement over traditional blockchain models prone to congestion during high demand periods.
Recent Developments Supporting Validator Coordination & Sharding
Ethereum's recent advancements underscore its commitment toward achieving full scalability with robust security measures:
Shard Canary Network (SCN): Launched in 2023 as an experimental environment for testing shard functionalities under real-world conditions before deploying on mainnet.
Mainnet Merge: Expected late 2023 or early 2024 marks a pivotal milestone where Ethereum will combine its existing PoW mainnet with the PoS-based Beacon Chain—a process known as "the Merge." This event will fully transition validation duties onto PoS while integrating sharding features progressively afterward.
These developments demonstrate continuous progress towards decentralization and efficiency but also highlight technical challenges such as ensuring secure cross-shard communication and maintaining validator incentives throughout complex upgrades.
Challenges Facing Validator Coordination & Shard Transition
While promising, transitioning from traditional blockchain architectures involves notable hurdles:
Technical Complexity: Implementing seamless communication between numerous shards requires sophisticated protocols; any vulnerabilities could compromise security.
Validator Participation Rates: The success hinges on active validator engagement; low participation could slow down progress or cause instability.
Network Security Risks: As complexity increases with sharding—and especially during transitional phases—the attack surface expands if not properly managed.
Regulatory Uncertainty: Evolving legal frameworks around cryptocurrencies may influence adoption rates among validators and users alike.
Addressing these issues demands rigorous testing—including testnets like SCN—and community support aligned with long-term development goals.
Key Facts About Ethereum’s Transition Timeline
| Event | Date/Expected Timeline | Significance |
|---|---|---|
| Launch of Beacon Chain | December 2020 | Foundation layer supporting staking |
| Launch of Shard Canary Network | 2023 | Testing environment for shard functionality |
| Expected Mainnet Merge | Late 2023 / Early 2024 | Full transition from PoW to PoS |
As these milestones approach, stakeholders closely monitor progress due to their impact on scalability improvements and overall network health.
Monitoring Future Developments in Validator Management & Sharding
Ethereum’s journey towards full-scale adoption relies heavily on effective coordination mechanisms provided by its consensus layer—the Beacon Chain—and successful implementation of sharding technology. Continuous upgrades aim not only at increasing transaction capacity but also at reinforcing decentralization by enabling more participants worldwide to become validators securely.
Staying informed about upcoming updates like protocol upgrades or testnet launches helps users understand how these changes might influence transaction speeds, costs (gas fees), security assurances, and overall user experience within this rapidly evolving ecosystem.
Final Thoughts: Navigating Growth Through Innovation
Ethereum's innovative approach via its beacon chain architecture exemplifies how layered coordination can transform blockchain networks into scalable platforms capable of supporting global applications—from decentralized finance (DeFi) projects to enterprise solutions—all while maintaining high-security standards through proof-of-stake validation processes combined with advanced sharding techniques.
By understanding how validator duties are managed alongside complex shard transitions—and keeping an eye on upcoming milestones—you can better appreciate both current capabilities and future potentialities shaping one of today’s most influential blockchain ecosystems
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
Everyone's asking when will ETH go up? 📊 Here's our Ethereum Price Prediction for 2025. Not financial advice. DYOR. 🧠 This video is for entertainment purposes only.


Ju.com Media
2025-08-04 08:44
Ethereum Price Prediction for 2025 📈
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
Which Platforms Support Smart Contracts?
Smart contracts are transforming the landscape of blockchain technology, enabling decentralized applications (dApps) to operate autonomously and securely. As this technology gains momentum, understanding which platforms support smart contracts is essential for developers, investors, and enthusiasts alike. This article provides a comprehensive overview of the leading blockchain platforms that facilitate smart contract deployment, their unique features, recent advancements, and potential challenges.
What Are Smart Contract Platforms?
A smart contract platform is a blockchain network that allows developers to write, deploy, and execute self-executing contracts coded with specific rules. These platforms provide the necessary infrastructure—such as programming languages, development tools, consensus mechanisms—to enable secure and transparent automation of contractual agreements without intermediaries.
The core value proposition of these platforms lies in their ability to ensure trustless transactions: once deployed on a blockchain like Ethereum or Solana, smart contracts cannot be altered or tampered with. This immutability guarantees transparency for all parties involved while reducing reliance on traditional legal systems.
Leading Blockchain Platforms Supporting Smart Contracts
Several prominent blockchain networks have emerged as leaders in supporting smart contract functionality. Each offers distinct advantages tailored to different use cases such as decentralized finance (DeFi), non-fungible tokens (NFTs), supply chain management, or enterprise solutions.
Ethereum: The Pioneer in Smart Contracts
Ethereum remains the most widely adopted platform for deploying smart contracts since its launch in 2015. It introduced Solidity—a purpose-built programming language designed specifically for writing complex dApps—and established a robust ecosystem that continues to drive innovation today.
Ethereum's extensive developer community has created thousands of decentralized applications across various sectors. Its open-source nature fosters continuous improvement through upgrades like Ethereum 2.0—aimed at enhancing scalability via proof-of-stake consensus and sharding techniques.
Binance Smart Chain (BSC): A Cost-Effective Alternative
Launched by Binance in 2020 as an alternative to Ethereum’s high transaction fees and congestion issues, Binance Smart Chain quickly gained popularity among developers seeking faster processing times at lower costs. BSC supports Solidity-based smart contracts similar to Ethereum but benefits from shorter block times and reduced fees due to its delegated proof-of-stake (DPoS) consensus mechanism using Binance Coin (BNB).
This platform has seen rapid growth in DeFi projects and NFT marketplaces owing to its affordability—making it attractive for startups aiming for quick deployment without sacrificing compatibility with existing tools.
Polkadot: Enabling Cross-Chain Compatibility
Polkadot introduces interoperability between multiple blockchains through its unique relay chain architecture combined with parachains—independent chains connected within the ecosystem. It supports deploying custom parachains capable of executing their own smart contracts using frameworks like Substrate or EVM-compatible modules.
By facilitating seamless communication across diverse networks—including those built on different protocols—Polkadot opens new avenues for cross-chain DeFi solutions and multi-chain NFTs while maintaining security through shared validators.
Solana: High-Speed Blockchain Platform
Solana distinguishes itself by offering extremely high throughput capabilities—processing thousands of transactions per second—with low latency thanks to its innovative proof-of-history combined with proof-of-stake consensus algorithms. Its architecture enables developers to build scalable dApps suitable for real-time gaming experiences or high-frequency trading platforms involving complex smart contract logic.
Despite being relatively newer compared to Ethereum or BSC, Solana’s focus on scalability has attracted significant developer interest seeking performance-intensive applications within DeFi ecosystems or NFT marketplaces demanding fast transaction finality.
Cardano: Emphasizing Formal Methods & Security
Cardano emphasizes academic rigor by employing formal verification methods during development processes; it uses Haskell-based Plutus language specifically designed for creating secure financial-grade smart contracts. Launched after years of peer-reviewed research efforts led by IOHK—the company behind Cardano—it aims at providing highly secure solutions suitable even for enterprise-level deployments where safety is paramount.
Recent Developments Enhancing Support For Smart Contracts
The landscape supporting these platforms continues evolving rapidly:
Ethereum 2.0 aims at addressing scalability issues through phased upgrades introducing proof-of-stake validation mechanisms alongside sharding techniques that distribute network load efficiently.
Binance Smart Chain experienced exponential growth during recent years due mainly to lower fees; ongoing improvements aim at increasing decentralization without compromising speed.
Polkadot's interoperability features now enable cross-chain asset transfers seamlessly across multiple networks—a critical feature fueling innovations like multi-chain DeFi protocols.
Solana’s focus on throughput capacity positions it well against competitors; recent partnerships have expanded its ecosystem into areas such as gaming NFTs.
Cardano continues emphasizing formal verification processes ensuring higher security standards vital when deploying large-scale financial applications.
Challenges Facing Blockchain Platforms Supporting Smart Contracts
While these platforms offer exciting opportunities—they also face notable hurdles:
Regulatory Uncertainty: Governments worldwide are still formulating policies around digital assets created via these networks; regulatory ambiguity could impact adoption rates.
Security Risks: Bugs within codebases can lead directly to financial losses—as seen historically with exploits like The DAO hack on Ethereum—and underscore the importance of rigorous auditing practices.
Environmental Concerns: Proof-of-work based systems consume significant energy; although many newer chains adopt eco-friendlier models such as proof-of-stake—which reduces environmental impact—the overall sustainability remains an ongoing discussion.
Future Outlook & Industry Trends
As demand grows—from enterprises adopting private blockchains supporting hybrid models—to individual users engaging with NFTs—the diversity among supported platforms will likely expand further:
Interoperability will become increasingly critical; projects like Polkadot exemplify this trend by enabling cross-network communication.
Scalability solutions will continue evolving—for example , Layer 2 rollups on Ethereum aim at alleviating congestion while maintaining security guarantees.
Security enhancements—including formal verification methods employed by Cardano—will be prioritized amid rising concerns over vulnerabilities.
Understanding which blockchain platforms support smart contracts helps stakeholders make informed decisions about deployment strategies aligned with project requirements concerning cost-efficiency, security standards, scalability needs,and future-proofing considerations.
By keeping abreast of developments across major players such as Ethereum, Binance Smart Chain, Polkadot, Solana, Cardano,* users can better navigate this dynamic space.* Whether you're developing new dApps or investing in innovative projects leveraging these technologies — knowing each platform's strengths ensures smarter choices aligned with industry trends toward decentralization and trustless automation.


JCUSER-WVMdslBw
2025-05-09 12:38
Which platforms support smart contracts?
Which Platforms Support Smart Contracts?
Smart contracts are transforming the landscape of blockchain technology, enabling decentralized applications (dApps) to operate autonomously and securely. As this technology gains momentum, understanding which platforms support smart contracts is essential for developers, investors, and enthusiasts alike. This article provides a comprehensive overview of the leading blockchain platforms that facilitate smart contract deployment, their unique features, recent advancements, and potential challenges.
What Are Smart Contract Platforms?
A smart contract platform is a blockchain network that allows developers to write, deploy, and execute self-executing contracts coded with specific rules. These platforms provide the necessary infrastructure—such as programming languages, development tools, consensus mechanisms—to enable secure and transparent automation of contractual agreements without intermediaries.
The core value proposition of these platforms lies in their ability to ensure trustless transactions: once deployed on a blockchain like Ethereum or Solana, smart contracts cannot be altered or tampered with. This immutability guarantees transparency for all parties involved while reducing reliance on traditional legal systems.
Leading Blockchain Platforms Supporting Smart Contracts
Several prominent blockchain networks have emerged as leaders in supporting smart contract functionality. Each offers distinct advantages tailored to different use cases such as decentralized finance (DeFi), non-fungible tokens (NFTs), supply chain management, or enterprise solutions.
Ethereum: The Pioneer in Smart Contracts
Ethereum remains the most widely adopted platform for deploying smart contracts since its launch in 2015. It introduced Solidity—a purpose-built programming language designed specifically for writing complex dApps—and established a robust ecosystem that continues to drive innovation today.
Ethereum's extensive developer community has created thousands of decentralized applications across various sectors. Its open-source nature fosters continuous improvement through upgrades like Ethereum 2.0—aimed at enhancing scalability via proof-of-stake consensus and sharding techniques.
Binance Smart Chain (BSC): A Cost-Effective Alternative
Launched by Binance in 2020 as an alternative to Ethereum’s high transaction fees and congestion issues, Binance Smart Chain quickly gained popularity among developers seeking faster processing times at lower costs. BSC supports Solidity-based smart contracts similar to Ethereum but benefits from shorter block times and reduced fees due to its delegated proof-of-stake (DPoS) consensus mechanism using Binance Coin (BNB).
This platform has seen rapid growth in DeFi projects and NFT marketplaces owing to its affordability—making it attractive for startups aiming for quick deployment without sacrificing compatibility with existing tools.
Polkadot: Enabling Cross-Chain Compatibility
Polkadot introduces interoperability between multiple blockchains through its unique relay chain architecture combined with parachains—independent chains connected within the ecosystem. It supports deploying custom parachains capable of executing their own smart contracts using frameworks like Substrate or EVM-compatible modules.
By facilitating seamless communication across diverse networks—including those built on different protocols—Polkadot opens new avenues for cross-chain DeFi solutions and multi-chain NFTs while maintaining security through shared validators.
Solana: High-Speed Blockchain Platform
Solana distinguishes itself by offering extremely high throughput capabilities—processing thousands of transactions per second—with low latency thanks to its innovative proof-of-history combined with proof-of-stake consensus algorithms. Its architecture enables developers to build scalable dApps suitable for real-time gaming experiences or high-frequency trading platforms involving complex smart contract logic.
Despite being relatively newer compared to Ethereum or BSC, Solana’s focus on scalability has attracted significant developer interest seeking performance-intensive applications within DeFi ecosystems or NFT marketplaces demanding fast transaction finality.
Cardano: Emphasizing Formal Methods & Security
Cardano emphasizes academic rigor by employing formal verification methods during development processes; it uses Haskell-based Plutus language specifically designed for creating secure financial-grade smart contracts. Launched after years of peer-reviewed research efforts led by IOHK—the company behind Cardano—it aims at providing highly secure solutions suitable even for enterprise-level deployments where safety is paramount.
Recent Developments Enhancing Support For Smart Contracts
The landscape supporting these platforms continues evolving rapidly:
Ethereum 2.0 aims at addressing scalability issues through phased upgrades introducing proof-of-stake validation mechanisms alongside sharding techniques that distribute network load efficiently.
Binance Smart Chain experienced exponential growth during recent years due mainly to lower fees; ongoing improvements aim at increasing decentralization without compromising speed.
Polkadot's interoperability features now enable cross-chain asset transfers seamlessly across multiple networks—a critical feature fueling innovations like multi-chain DeFi protocols.
Solana’s focus on throughput capacity positions it well against competitors; recent partnerships have expanded its ecosystem into areas such as gaming NFTs.
Cardano continues emphasizing formal verification processes ensuring higher security standards vital when deploying large-scale financial applications.
Challenges Facing Blockchain Platforms Supporting Smart Contracts
While these platforms offer exciting opportunities—they also face notable hurdles:
Regulatory Uncertainty: Governments worldwide are still formulating policies around digital assets created via these networks; regulatory ambiguity could impact adoption rates.
Security Risks: Bugs within codebases can lead directly to financial losses—as seen historically with exploits like The DAO hack on Ethereum—and underscore the importance of rigorous auditing practices.
Environmental Concerns: Proof-of-work based systems consume significant energy; although many newer chains adopt eco-friendlier models such as proof-of-stake—which reduces environmental impact—the overall sustainability remains an ongoing discussion.
Future Outlook & Industry Trends
As demand grows—from enterprises adopting private blockchains supporting hybrid models—to individual users engaging with NFTs—the diversity among supported platforms will likely expand further:
Interoperability will become increasingly critical; projects like Polkadot exemplify this trend by enabling cross-network communication.
Scalability solutions will continue evolving—for example , Layer 2 rollups on Ethereum aim at alleviating congestion while maintaining security guarantees.
Security enhancements—including formal verification methods employed by Cardano—will be prioritized amid rising concerns over vulnerabilities.
Understanding which blockchain platforms support smart contracts helps stakeholders make informed decisions about deployment strategies aligned with project requirements concerning cost-efficiency, security standards, scalability needs,and future-proofing considerations.
By keeping abreast of developments across major players such as Ethereum, Binance Smart Chain, Polkadot, Solana, Cardano,* users can better navigate this dynamic space.* Whether you're developing new dApps or investing in innovative projects leveraging these technologies — knowing each platform's strengths ensures smarter choices aligned with industry trends toward decentralization and trustless automation.
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
What Is a Layer-2 Scaling Solution?
Understanding the Basics of Blockchain Scalability
Blockchain networks like Ethereum have revolutionized digital transactions by providing decentralized, transparent, and secure platforms. However, as these networks grow in popularity, they face significant scalability challenges. The core issue lies in the limited capacity of the main blockchain (layer-1), which can process only a finite number of transactions per second. This bottleneck results in high transaction fees, slow confirmation times, and network congestion—problems that hinder mainstream adoption.
Layer-2 scaling solutions are designed to address these limitations by operating on top of the primary blockchain. Instead of relying solely on on-chain processing, they handle most transactions off-chain or through secondary protocols. This approach significantly increases transaction throughput while maintaining security and decentralization standards.
How Layer-2 Solutions Enhance Blockchain Performance
Layer-2 solutions work by shifting transactional load away from the main chain to secondary layers or off-chain channels. These methods enable users to conduct numerous transactions quickly and cheaply without overburdening the base layer network.
For example, some layer-2 protocols bundle multiple transactions into a single batch before submitting it back to the main chain for settlement. This batching reduces gas fees—a critical factor considering Ethereum's fluctuating costs—and accelerates transaction confirmation times.
Security remains paramount; therefore, most layer-2 solutions leverage cryptographic proofs or mechanisms anchored to the underlying blockchain’s security model. This ensures that even though transactions occur off-chain or on sidechains, their integrity is verifiable and trustworthy.
Main Types of Layer-2 Scaling Solutions
There are several approaches within layer-2 technology tailored for different use cases:
State Channels:
State channels facilitate direct interactions between two parties without recording every transaction on-chain immediately. Participants open a channel by locking funds into a multi-signature contract; they then perform multiple off-chain exchanges with instant finality. Only when closing the channel do they broadcast an aggregated state update to settle balances on Ethereum’s mainnet.- Examples include Raiden Network (Ethereum) and Lightning Network (Bitcoin).
- Use cases: Micropayments, gaming microtransactions.
Sidechains:
Sidechains are independent blockchains linked securely to their parent chain via bridges or two-way pegs. They process transactions separately but periodically synchronize with Ethereum’s mainnet for final settlement.- Examples include Cosmos Hub and Polkadot parachains.
- Use cases: Specialized applications requiring custom consensus mechanisms or faster throughput.
Rollups:
Rollups aggregate hundreds or thousands of individual transactions into one batch processed on Ethereum's mainnet as a single proof—either optimistic or zero-knowledge-based.- Optimistic Rollups assume validity unless challenged; ZK-Rollups generate cryptographic proofs confirming correctness.
- Examples include Optimism and Arbitrum.
- Benefits include reduced gas costs while preserving security guarantees similar to those of Ethereum itself.
Recent Developments Shaping Layer-2 Adoption
The transition of Ethereum from proof-of-work (PoW) to proof-of-stake (PoS)—known as "The Merge"—has been pivotal in creating an environment more conducive for scaling solutions like rollups and state channels due to lower energy consumption and increased efficiency.
Major projects have made significant strides:
- Ethereum's Shift: The move towards PoS enhances scalability potential alongside layer-two implementations by reducing network congestion at its core.
- Rollup Adoption: Platforms such as Optimism and Arbitrum have seen rapid growth with numerous DeFi projects integrating them for faster trading experiences at lower costs.
- Bitcoin’s Lightning Network: Although not directly related to Ethereum-focused solutions, Lightning has demonstrated how effective off-chain payment channels can be at scale—serving as inspiration across blockchain ecosystems.
- Interoperability Challenges: As various layer-two protocols emerge independently, ensuring seamless interoperability becomes crucial—a focus area for developers aiming toward unified user experiences across different chains.
Security Considerations & Regulatory Outlook
While layer-two solutions offer impressive scalability benefits—they also introduce new risks that must be carefully managed:
- Security vulnerabilities may arise if smart contracts governing state channels or sidechains contain bugs.
- Centralization concerns exist where certain rollup operators could potentially influence outcomes if not properly decentralized.
- Regulatory scrutiny is increasing around off-chain activities; questions about jurisdictional oversight could impact future deployment strategies especially concerning privacy compliance laws like GDPR.
These factors underscore why rigorous audits, transparent governance models, and ongoing research are vital components in building trustworthy scalable infrastructure within blockchain ecosystems.
The Future Role Of Layer-2 Solutions In Blockchain Ecosystems
As demand grows for faster yet secure digital assets transfer methods—particularly within DeFi platforms—the importance of scalable infrastructure becomes undeniable. Layer-two technologies will likely continue evolving through innovations such as zk-rollups improving privacy features alongside performance gains while enhancing interoperability standards among diverse chains remains an active research area.
By enabling higher throughput without sacrificing decentralization principles fundamental to blockchain technology—their role is central not just in easing current limitations but also paving pathways toward mass adoption across industries—from finance & supply chain management—to gaming & identity verification systems.
In essence,
Layer-two scaling solutions represent a critical evolution point for blockchain technology — balancing speed with security — making them indispensable tools shaping future decentralized networks' landscape.


Lo
2025-05-15 02:42
What is a layer-2 scaling solution?
What Is a Layer-2 Scaling Solution?
Understanding the Basics of Blockchain Scalability
Blockchain networks like Ethereum have revolutionized digital transactions by providing decentralized, transparent, and secure platforms. However, as these networks grow in popularity, they face significant scalability challenges. The core issue lies in the limited capacity of the main blockchain (layer-1), which can process only a finite number of transactions per second. This bottleneck results in high transaction fees, slow confirmation times, and network congestion—problems that hinder mainstream adoption.
Layer-2 scaling solutions are designed to address these limitations by operating on top of the primary blockchain. Instead of relying solely on on-chain processing, they handle most transactions off-chain or through secondary protocols. This approach significantly increases transaction throughput while maintaining security and decentralization standards.
How Layer-2 Solutions Enhance Blockchain Performance
Layer-2 solutions work by shifting transactional load away from the main chain to secondary layers or off-chain channels. These methods enable users to conduct numerous transactions quickly and cheaply without overburdening the base layer network.
For example, some layer-2 protocols bundle multiple transactions into a single batch before submitting it back to the main chain for settlement. This batching reduces gas fees—a critical factor considering Ethereum's fluctuating costs—and accelerates transaction confirmation times.
Security remains paramount; therefore, most layer-2 solutions leverage cryptographic proofs or mechanisms anchored to the underlying blockchain’s security model. This ensures that even though transactions occur off-chain or on sidechains, their integrity is verifiable and trustworthy.
Main Types of Layer-2 Scaling Solutions
There are several approaches within layer-2 technology tailored for different use cases:
State Channels:
State channels facilitate direct interactions between two parties without recording every transaction on-chain immediately. Participants open a channel by locking funds into a multi-signature contract; they then perform multiple off-chain exchanges with instant finality. Only when closing the channel do they broadcast an aggregated state update to settle balances on Ethereum’s mainnet.- Examples include Raiden Network (Ethereum) and Lightning Network (Bitcoin).
- Use cases: Micropayments, gaming microtransactions.
Sidechains:
Sidechains are independent blockchains linked securely to their parent chain via bridges or two-way pegs. They process transactions separately but periodically synchronize with Ethereum’s mainnet for final settlement.- Examples include Cosmos Hub and Polkadot parachains.
- Use cases: Specialized applications requiring custom consensus mechanisms or faster throughput.
Rollups:
Rollups aggregate hundreds or thousands of individual transactions into one batch processed on Ethereum's mainnet as a single proof—either optimistic or zero-knowledge-based.- Optimistic Rollups assume validity unless challenged; ZK-Rollups generate cryptographic proofs confirming correctness.
- Examples include Optimism and Arbitrum.
- Benefits include reduced gas costs while preserving security guarantees similar to those of Ethereum itself.
Recent Developments Shaping Layer-2 Adoption
The transition of Ethereum from proof-of-work (PoW) to proof-of-stake (PoS)—known as "The Merge"—has been pivotal in creating an environment more conducive for scaling solutions like rollups and state channels due to lower energy consumption and increased efficiency.
Major projects have made significant strides:
- Ethereum's Shift: The move towards PoS enhances scalability potential alongside layer-two implementations by reducing network congestion at its core.
- Rollup Adoption: Platforms such as Optimism and Arbitrum have seen rapid growth with numerous DeFi projects integrating them for faster trading experiences at lower costs.
- Bitcoin’s Lightning Network: Although not directly related to Ethereum-focused solutions, Lightning has demonstrated how effective off-chain payment channels can be at scale—serving as inspiration across blockchain ecosystems.
- Interoperability Challenges: As various layer-two protocols emerge independently, ensuring seamless interoperability becomes crucial—a focus area for developers aiming toward unified user experiences across different chains.
Security Considerations & Regulatory Outlook
While layer-two solutions offer impressive scalability benefits—they also introduce new risks that must be carefully managed:
- Security vulnerabilities may arise if smart contracts governing state channels or sidechains contain bugs.
- Centralization concerns exist where certain rollup operators could potentially influence outcomes if not properly decentralized.
- Regulatory scrutiny is increasing around off-chain activities; questions about jurisdictional oversight could impact future deployment strategies especially concerning privacy compliance laws like GDPR.
These factors underscore why rigorous audits, transparent governance models, and ongoing research are vital components in building trustworthy scalable infrastructure within blockchain ecosystems.
The Future Role Of Layer-2 Solutions In Blockchain Ecosystems
As demand grows for faster yet secure digital assets transfer methods—particularly within DeFi platforms—the importance of scalable infrastructure becomes undeniable. Layer-two technologies will likely continue evolving through innovations such as zk-rollups improving privacy features alongside performance gains while enhancing interoperability standards among diverse chains remains an active research area.
By enabling higher throughput without sacrificing decentralization principles fundamental to blockchain technology—their role is central not just in easing current limitations but also paving pathways toward mass adoption across industries—from finance & supply chain management—to gaming & identity verification systems.
In essence,
Layer-two scaling solutions represent a critical evolution point for blockchain technology — balancing speed with security — making them indispensable tools shaping future decentralized networks' landscape.
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
Platforms Supporting Smart Contracts: A Comprehensive Overview
Smart contracts are transforming the way digital agreements are created, executed, and enforced. These self-executing contracts, embedded with code that automatically enforces terms, rely heavily on blockchain platforms to operate securely and efficiently. Understanding which platforms support smart contracts—and their unique features—is essential for developers, investors, and enthusiasts aiming to navigate the decentralized ecosystem effectively.
What Are Smart Contracts?
Smart contracts are programmable agreements that automatically execute predefined actions once certain conditions are met. Unlike traditional contracts requiring intermediaries such as lawyers or banks for enforcement, smart contracts leverage blockchain technology's transparency and immutability to ensure trustless execution. They can facilitate a wide range of applications—from simple token transfers to complex financial derivatives—making them foundational components of decentralized applications (dApps).
The Role of Blockchain Platforms in Supporting Smart Contracts
Blockchain platforms serve as the infrastructure enabling smart contract deployment and execution. These platforms provide the necessary programming environments, consensus mechanisms, security protocols, and interoperability features crucial for building scalable dApps across various industries like finance (DeFi), gaming, supply chain management, and more.
Different blockchain networks offer varying capabilities regarding smart contract support—some focus on scalability and speed; others emphasize security or interoperability. As a result, selecting an appropriate platform depends on project requirements such as transaction throughput needs or compatibility with existing systems.
Leading Blockchain Platforms Supporting Smart Contracts
Ethereum: The Pioneer in Smart Contract Support
Launched in 2015 by Vitalik Buterin, Ethereum is widely regarded as the first blockchain platform designed explicitly for supporting smart contracts at scale. Its robust ecosystem has fostered countless innovations within DeFi (Decentralized Finance), NFTs (Non-Fungible Tokens), gaming dApps—and continues to be a dominant force despite scalability challenges.
Ethereum’s programming language Solidity allows developers to write complex logic into their smart contracts easily. Its proof-of-work consensus mechanism initially provided security but faced criticism over energy consumption issues—a concern addressed by its ongoing transition toward Ethereum 2.0’s proof-of-stake model aimed at improving scalability while reducing environmental impact.
Binance Smart Chain: Fast & Cost-Effective Alternative
Developed by Binance in 2020 as an alternative to Ethereum’s network congestion issues—such as high gas fees—Binance Smart Chain (BSC) offers faster transaction speeds coupled with lower costs without sacrificing compatibility with existing tools like MetaMask or Remix IDE.
BSC supports Solidity-based smart contracts similar to Ethereum but benefits from a delegated proof-of-stake consensus algorithm that enhances throughput efficiency. This makes BSC particularly attractive for developers seeking rapid deployment cycles or users prioritizing low-cost transactions within DeFi projects or NFT marketplaces.
Polkadot: Enabling Interoperability Between Blockchains
Polkadot introduces a novel approach by facilitating communication between different blockchains through its parachain architecture—a network of parallel chains connected via relay chains ensuring shared security and data transfer capabilities.
Supporting multiple languages—including ink! (Rust-based)—Polkadot enables deploying interoperable smart contracts across diverse ecosystems simultaneously. This cross-chain functionality addresses one of blockchain technology's critical limitations: siloed networks unable to communicate seamlessly—a barrier hindering widespread adoption of decentralized solutions.
Solana: High-Performance Blockchain for Scalability
Designed specifically for high-throughput applications like DeFi protocols or NFT marketplaces requiring rapid transaction processing—Solana employs innovative Proof-of-Stake combined with Proof-of-History mechanisms allowing it to process thousands of transactions per second with minimal latency.
Developers can write Solana programs using Rust or C language frameworks; this flexibility has led many projects seeking scalable solutions away from congested networks like Ethereum towards Solana’s fast environment suitable for real-time applications such as gaming dApps or high-frequency trading platforms.
Cardano: Focused on Security & Scalability
Cardano emphasizes formal verification methods rooted in academic research principles aimed at creating highly secure yet scalable blockchain infrastructure capable of supporting complex decentralized apps over time confidently.Its native scripting language Plutus enables writing secure smart contract logic based on Haskell—a functional programming language known for robustness against bugs.Recent developments include launching sidechains that extend Cardano's capabilities further while maintaining core decentralization principles vital for enterprise-grade deployments across sectors including finance and healthcare sectors needing compliant solutions aligned with regulatory standards globally.
How Do These Platforms Differ?
While all these platforms support deploying self-executing code via their respective ecosystems—their differences lie mainly in:
- Consensus algorithms (Proof-of-Work vs Proof-of-Stake vs Delegated Stake)
- Transaction speeds
- Cost structures
- Interoperability features
- Programming languages supported
For example:Ethereum remains dominant due to its extensive developer community but faces scalability hurdles.Binance Smart Chain offers speed at lower costs but may compromise some decentralization aspects.Polkadot excels at cross-chain communication but is relatively newer.Solana, known for speed; however it faces concerns about network stability during peak loads.Cardano, emphasizing formal verification ensures higher assurance levels suitable especially where compliance matters.
Challenges Facing Platform Adoption
Despite technological advancements supporting smarter contract deployment:
- Security vulnerabilities remain prevalent; poorly written code can lead to exploits causing significant financial losses—as seen in past hacks involving flash loan attacks.
- Scalability constraints continue limiting user experience during peak demand periods leading developers toward layer-two solutions like rollups.
- The evolving regulatory landscape adds uncertainty around compliance requirements affecting how these technologies develop long-term strategies.
- Interoperability remains an ongoing challenge; seamless communication among diverse blockchains is crucial yet still under active development.
Future Outlook & Industry Trends
The future points toward increasingly sophisticated multi-chain ecosystems where interoperability becomes standard rather than exception—with projects like Polkadot leading this charge—and improvements in scalability through Layer 2 solutions integrated into mainnets will likely address current bottlenecks significantly.
Furthermore:
- Transition phases such as Ethereum 2.o's move from PoW/PoS hybrid models will reshape network performance.
- Growing emphasis on security audits will enhance trustworthiness among users engaging with complex dApps
- Regulatory clarity could foster broader institutional adoption beyond crypto-native communities
Key Takeaways
Understanding which blockchain platforms support smart contracts involves evaluating factors such as speed requirements, cost considerations, security needs,and interoperability goals:
- Ethereum remains the most established platform, offering extensive developer resources despite facing scaling challenges;
- Binance Smart Chain provides faster transactions at lower fees, making it popular among DeFi startups;
- Polkadot facilitates cross-chain interactions, opening new opportunities across multiple ecosystems;
- Solana delivers high throughput idealfor real-time apps, though stability concerns persist;
- Cardano emphasizes formal methods ensuring secure deployments, suited especially where compliance matters most.
By aligning project goals with each platform’s strengths—and staying informed about ongoing upgrades—the industry can harness these technologies' full potential while addressing inherent limitations responsibly.
This overview aims not only to inform readers about current options supporting smart contract development but also highlights emerging trends shaping future innovations within this rapidly evolving field — empowering stakeholders across industries committed towards building transparent,decentralized systems grounded firmly in proven technological foundations..


Lo
2025-05-14 05:59
Which platforms support smart contracts?
Platforms Supporting Smart Contracts: A Comprehensive Overview
Smart contracts are transforming the way digital agreements are created, executed, and enforced. These self-executing contracts, embedded with code that automatically enforces terms, rely heavily on blockchain platforms to operate securely and efficiently. Understanding which platforms support smart contracts—and their unique features—is essential for developers, investors, and enthusiasts aiming to navigate the decentralized ecosystem effectively.
What Are Smart Contracts?
Smart contracts are programmable agreements that automatically execute predefined actions once certain conditions are met. Unlike traditional contracts requiring intermediaries such as lawyers or banks for enforcement, smart contracts leverage blockchain technology's transparency and immutability to ensure trustless execution. They can facilitate a wide range of applications—from simple token transfers to complex financial derivatives—making them foundational components of decentralized applications (dApps).
The Role of Blockchain Platforms in Supporting Smart Contracts
Blockchain platforms serve as the infrastructure enabling smart contract deployment and execution. These platforms provide the necessary programming environments, consensus mechanisms, security protocols, and interoperability features crucial for building scalable dApps across various industries like finance (DeFi), gaming, supply chain management, and more.
Different blockchain networks offer varying capabilities regarding smart contract support—some focus on scalability and speed; others emphasize security or interoperability. As a result, selecting an appropriate platform depends on project requirements such as transaction throughput needs or compatibility with existing systems.
Leading Blockchain Platforms Supporting Smart Contracts
Ethereum: The Pioneer in Smart Contract Support
Launched in 2015 by Vitalik Buterin, Ethereum is widely regarded as the first blockchain platform designed explicitly for supporting smart contracts at scale. Its robust ecosystem has fostered countless innovations within DeFi (Decentralized Finance), NFTs (Non-Fungible Tokens), gaming dApps—and continues to be a dominant force despite scalability challenges.
Ethereum’s programming language Solidity allows developers to write complex logic into their smart contracts easily. Its proof-of-work consensus mechanism initially provided security but faced criticism over energy consumption issues—a concern addressed by its ongoing transition toward Ethereum 2.0’s proof-of-stake model aimed at improving scalability while reducing environmental impact.
Binance Smart Chain: Fast & Cost-Effective Alternative
Developed by Binance in 2020 as an alternative to Ethereum’s network congestion issues—such as high gas fees—Binance Smart Chain (BSC) offers faster transaction speeds coupled with lower costs without sacrificing compatibility with existing tools like MetaMask or Remix IDE.
BSC supports Solidity-based smart contracts similar to Ethereum but benefits from a delegated proof-of-stake consensus algorithm that enhances throughput efficiency. This makes BSC particularly attractive for developers seeking rapid deployment cycles or users prioritizing low-cost transactions within DeFi projects or NFT marketplaces.
Polkadot: Enabling Interoperability Between Blockchains
Polkadot introduces a novel approach by facilitating communication between different blockchains through its parachain architecture—a network of parallel chains connected via relay chains ensuring shared security and data transfer capabilities.
Supporting multiple languages—including ink! (Rust-based)—Polkadot enables deploying interoperable smart contracts across diverse ecosystems simultaneously. This cross-chain functionality addresses one of blockchain technology's critical limitations: siloed networks unable to communicate seamlessly—a barrier hindering widespread adoption of decentralized solutions.
Solana: High-Performance Blockchain for Scalability
Designed specifically for high-throughput applications like DeFi protocols or NFT marketplaces requiring rapid transaction processing—Solana employs innovative Proof-of-Stake combined with Proof-of-History mechanisms allowing it to process thousands of transactions per second with minimal latency.
Developers can write Solana programs using Rust or C language frameworks; this flexibility has led many projects seeking scalable solutions away from congested networks like Ethereum towards Solana’s fast environment suitable for real-time applications such as gaming dApps or high-frequency trading platforms.
Cardano: Focused on Security & Scalability
Cardano emphasizes formal verification methods rooted in academic research principles aimed at creating highly secure yet scalable blockchain infrastructure capable of supporting complex decentralized apps over time confidently.Its native scripting language Plutus enables writing secure smart contract logic based on Haskell—a functional programming language known for robustness against bugs.Recent developments include launching sidechains that extend Cardano's capabilities further while maintaining core decentralization principles vital for enterprise-grade deployments across sectors including finance and healthcare sectors needing compliant solutions aligned with regulatory standards globally.
How Do These Platforms Differ?
While all these platforms support deploying self-executing code via their respective ecosystems—their differences lie mainly in:
- Consensus algorithms (Proof-of-Work vs Proof-of-Stake vs Delegated Stake)
- Transaction speeds
- Cost structures
- Interoperability features
- Programming languages supported
For example:Ethereum remains dominant due to its extensive developer community but faces scalability hurdles.Binance Smart Chain offers speed at lower costs but may compromise some decentralization aspects.Polkadot excels at cross-chain communication but is relatively newer.Solana, known for speed; however it faces concerns about network stability during peak loads.Cardano, emphasizing formal verification ensures higher assurance levels suitable especially where compliance matters.
Challenges Facing Platform Adoption
Despite technological advancements supporting smarter contract deployment:
- Security vulnerabilities remain prevalent; poorly written code can lead to exploits causing significant financial losses—as seen in past hacks involving flash loan attacks.
- Scalability constraints continue limiting user experience during peak demand periods leading developers toward layer-two solutions like rollups.
- The evolving regulatory landscape adds uncertainty around compliance requirements affecting how these technologies develop long-term strategies.
- Interoperability remains an ongoing challenge; seamless communication among diverse blockchains is crucial yet still under active development.
Future Outlook & Industry Trends
The future points toward increasingly sophisticated multi-chain ecosystems where interoperability becomes standard rather than exception—with projects like Polkadot leading this charge—and improvements in scalability through Layer 2 solutions integrated into mainnets will likely address current bottlenecks significantly.
Furthermore:
- Transition phases such as Ethereum 2.o's move from PoW/PoS hybrid models will reshape network performance.
- Growing emphasis on security audits will enhance trustworthiness among users engaging with complex dApps
- Regulatory clarity could foster broader institutional adoption beyond crypto-native communities
Key Takeaways
Understanding which blockchain platforms support smart contracts involves evaluating factors such as speed requirements, cost considerations, security needs,and interoperability goals:
- Ethereum remains the most established platform, offering extensive developer resources despite facing scaling challenges;
- Binance Smart Chain provides faster transactions at lower fees, making it popular among DeFi startups;
- Polkadot facilitates cross-chain interactions, opening new opportunities across multiple ecosystems;
- Solana delivers high throughput idealfor real-time apps, though stability concerns persist;
- Cardano emphasizes formal methods ensuring secure deployments, suited especially where compliance matters most.
By aligning project goals with each platform’s strengths—and staying informed about ongoing upgrades—the industry can harness these technologies' full potential while addressing inherent limitations responsibly.
This overview aims not only to inform readers about current options supporting smart contract development but also highlights emerging trends shaping future innovations within this rapidly evolving field — empowering stakeholders across industries committed towards building transparent,decentralized systems grounded firmly in proven technological foundations..
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.
Cross-Chain Bridges Connecting Solana (SOL), Ethereum (ETH), and Avalanche (AVAX)
Understanding Cross-Chain Bridges in Blockchain Ecosystems
Cross-chain bridges are essential components of the modern blockchain landscape, enabling interoperability between different networks. They serve as connectors that facilitate the transfer of digital assets, such as tokens and NFTs, across diverse blockchain platforms. This capability is vital for expanding decentralized finance (DeFi) applications, enhancing liquidity, and fostering innovation within the crypto space.
By allowing users to move assets seamlessly from one blockchain to another, cross-chain bridges help overcome limitations inherent in isolated networks. For example, Ethereum’s widespread adoption often leads to congestion and high transaction fees. Bridging assets to faster or more scalable chains like Solana or Avalanche can mitigate these issues while maintaining access to a broad ecosystem of DeFi protocols.
Key Cross-Chain Bridges Supporting Solana and Ethereum
Several prominent protocols enable asset transfers between Solana (SOL) and Ethereum (ETH). These include Connext Network, Multichain, and Celer Network—each offering unique features tailored for security, scalability, and user experience.
Connext Network
Launched in 2020, Connext is a decentralized protocol supporting multiple blockchains including Solana and Ethereum. It facilitates fast asset transfers with low latency by leveraging state channels—a technology that allows transactions off-chain before settling on the main chain. Recently expanded support has increased its utility within DeFi markets by enabling seamless movement of tokens like USDC or wrapped ETH across these networks.
Multichain
Originally launched in 2021 under different branding but now known as Multichain—this protocol supports an extensive range of blockchains beyond just SOL and ETH. Its primary focus is on providing secure cross-chain asset transfers with minimal delays. Recent updates have improved scalability features significantly in 2024; this has attracted more developers seeking reliable infrastructure for multi-network DeFi applications.
Celer Network
Celer Network offers a suite of tools designed for building scalable cross-chain applications since its inception in 2020. It supports both Solana and Ethereum among other chains through its layer-2 scaling solutions called State Channels & Virtual Chains. The platform’s recent emphasis on scalability enhancements has led to increased adoption among DeFi projects aiming for high throughput without compromising security.
Connecting Solana with Avalanche: The Role of Specialized Bridges
While bridging SOL directly with ETH involves well-established protocols like Connext or Multichain, connecting Solana with Avalanche introduces additional options tailored specifically for interoperability between these two high-performance chains.
Avalanche Bridge: Native Solution for Asset Transfers
Launched by the Avalanche team in 2022, the Avalanche Bridge provides native support for transferring assets such as AVAX tokens between Avalanche’s network and other blockchains including Solana. Its design emphasizes security while ensuring quick transaction finality—making it popular among NFT marketplaces and DeFi platforms seeking efficient cross-platform liquidity flows.
Supporting Protocols: Connext & Multichain
Both Connext Network and Multichain extend their support beyond SOL-Ethereum interactions to include SOL-Avalanche transfers as well:
Connext offers decentralized solutions that prioritize security during asset migration.
Multichain ensures robust performance through continuous protocol upgrades aimed at improving scalability when moving assets across these chains.
These integrations allow users to leverage each network's strengths—such as Solana's speed or Avalanche's low fees—in their broader crypto activities.
Implications of Cross-Chain Connectivity
The development of interconnected ecosystems involving Solana, Ethereum, and Avalanche carries significant implications:
Enhanced Interoperability: Users can access diverse dApps spanning multiple networks without needing separate wallets or complex processes.
Increased Scalability: Transferring assets onto faster chains reduces congestion on congested networks like Ethereum during peak periods.
Broader Market Access: Asset mobility enables participation across various NFT marketplaces or DeFi protocols regardless of underlying blockchain constraints.
Security Considerations: While benefits are clear — especially regarding efficiency — risks associated with bridge exploits remain prevalent due to protocol complexity.
Regulatory Challenges: As cross-chain activity grows exponentially; regulators may scrutinize these mechanisms more closely due to potential misuse scenarios such as money laundering or unregulated token swaps.
Timeline Highlights & Recent Developments
Understanding key milestones helps contextualize current capabilities:
Connext was launched in 2020; recent updates have enhanced multi-assets support along with improved security features throughout 2023.
Multichain debuted officially around 2021; its latest upgrade cycle occurred early 2024 focusing heavily on scalability improvements which boosted user confidence.
Celer Network, also starting operations in late 2019/early 2020s’, focused heavily last year on increasing throughput capacity via layer-two scaling techniques.
Avalanche Bridge, introduced mid-last decade but saw significant growth after major updates rolled out into early this year—including expanded supported tokens facilitating broader use cases especially within NFT sectors.
Risks & Future Outlook
Despite promising advancements toward seamless interoperability among major blockchains like SOL/Ethereum/AVAX—the landscape isn’t without challenges:
Security vulnerabilities: Cross-chain bridges are complex systems susceptible to exploits if not properly secured—a concern highlighted by past incidents involving bridge hacks resulting in substantial losses.*
Regulatory environment: As governments worldwide develop frameworks governing digital assets’ transferability across borders—and increasingly scrutinize crypto exchanges—the regulatory landscape could impact how these bridges operate moving forward.*
Looking ahead:
The continued evolution will likely see further integration efforts driven by industry collaborations aiming at reducing risks while expanding functionality—for example through standardized protocols that enhance trustworthiness—and possibly integrating emerging technologies such as zk-rollups or optimistic rollups into bridge architectures.
By understanding how specific cross-chain bridges connect prominent blockchains like Solana (SOL), Ethereum (ETH),and Avalanche (AVAX), stakeholders—from developers to investors—can better navigate this rapidly evolving ecosystem while appreciating both opportunitiesand inherent risks involvedin multi-network operations


kai
2025-05-14 21:31
What cross-chain bridges connect Solana (SOL) with Ethereum (ETH) and Avalanche (AVAX)?
Cross-Chain Bridges Connecting Solana (SOL), Ethereum (ETH), and Avalanche (AVAX)
Understanding Cross-Chain Bridges in Blockchain Ecosystems
Cross-chain bridges are essential components of the modern blockchain landscape, enabling interoperability between different networks. They serve as connectors that facilitate the transfer of digital assets, such as tokens and NFTs, across diverse blockchain platforms. This capability is vital for expanding decentralized finance (DeFi) applications, enhancing liquidity, and fostering innovation within the crypto space.
By allowing users to move assets seamlessly from one blockchain to another, cross-chain bridges help overcome limitations inherent in isolated networks. For example, Ethereum’s widespread adoption often leads to congestion and high transaction fees. Bridging assets to faster or more scalable chains like Solana or Avalanche can mitigate these issues while maintaining access to a broad ecosystem of DeFi protocols.
Key Cross-Chain Bridges Supporting Solana and Ethereum
Several prominent protocols enable asset transfers between Solana (SOL) and Ethereum (ETH). These include Connext Network, Multichain, and Celer Network—each offering unique features tailored for security, scalability, and user experience.
Connext Network
Launched in 2020, Connext is a decentralized protocol supporting multiple blockchains including Solana and Ethereum. It facilitates fast asset transfers with low latency by leveraging state channels—a technology that allows transactions off-chain before settling on the main chain. Recently expanded support has increased its utility within DeFi markets by enabling seamless movement of tokens like USDC or wrapped ETH across these networks.
Multichain
Originally launched in 2021 under different branding but now known as Multichain—this protocol supports an extensive range of blockchains beyond just SOL and ETH. Its primary focus is on providing secure cross-chain asset transfers with minimal delays. Recent updates have improved scalability features significantly in 2024; this has attracted more developers seeking reliable infrastructure for multi-network DeFi applications.
Celer Network
Celer Network offers a suite of tools designed for building scalable cross-chain applications since its inception in 2020. It supports both Solana and Ethereum among other chains through its layer-2 scaling solutions called State Channels & Virtual Chains. The platform’s recent emphasis on scalability enhancements has led to increased adoption among DeFi projects aiming for high throughput without compromising security.
Connecting Solana with Avalanche: The Role of Specialized Bridges
While bridging SOL directly with ETH involves well-established protocols like Connext or Multichain, connecting Solana with Avalanche introduces additional options tailored specifically for interoperability between these two high-performance chains.
Avalanche Bridge: Native Solution for Asset Transfers
Launched by the Avalanche team in 2022, the Avalanche Bridge provides native support for transferring assets such as AVAX tokens between Avalanche’s network and other blockchains including Solana. Its design emphasizes security while ensuring quick transaction finality—making it popular among NFT marketplaces and DeFi platforms seeking efficient cross-platform liquidity flows.
Supporting Protocols: Connext & Multichain
Both Connext Network and Multichain extend their support beyond SOL-Ethereum interactions to include SOL-Avalanche transfers as well:
Connext offers decentralized solutions that prioritize security during asset migration.
Multichain ensures robust performance through continuous protocol upgrades aimed at improving scalability when moving assets across these chains.
These integrations allow users to leverage each network's strengths—such as Solana's speed or Avalanche's low fees—in their broader crypto activities.
Implications of Cross-Chain Connectivity
The development of interconnected ecosystems involving Solana, Ethereum, and Avalanche carries significant implications:
Enhanced Interoperability: Users can access diverse dApps spanning multiple networks without needing separate wallets or complex processes.
Increased Scalability: Transferring assets onto faster chains reduces congestion on congested networks like Ethereum during peak periods.
Broader Market Access: Asset mobility enables participation across various NFT marketplaces or DeFi protocols regardless of underlying blockchain constraints.
Security Considerations: While benefits are clear — especially regarding efficiency — risks associated with bridge exploits remain prevalent due to protocol complexity.
Regulatory Challenges: As cross-chain activity grows exponentially; regulators may scrutinize these mechanisms more closely due to potential misuse scenarios such as money laundering or unregulated token swaps.
Timeline Highlights & Recent Developments
Understanding key milestones helps contextualize current capabilities:
Connext was launched in 2020; recent updates have enhanced multi-assets support along with improved security features throughout 2023.
Multichain debuted officially around 2021; its latest upgrade cycle occurred early 2024 focusing heavily on scalability improvements which boosted user confidence.
Celer Network, also starting operations in late 2019/early 2020s’, focused heavily last year on increasing throughput capacity via layer-two scaling techniques.
Avalanche Bridge, introduced mid-last decade but saw significant growth after major updates rolled out into early this year—including expanded supported tokens facilitating broader use cases especially within NFT sectors.
Risks & Future Outlook
Despite promising advancements toward seamless interoperability among major blockchains like SOL/Ethereum/AVAX—the landscape isn’t without challenges:
Security vulnerabilities: Cross-chain bridges are complex systems susceptible to exploits if not properly secured—a concern highlighted by past incidents involving bridge hacks resulting in substantial losses.*
Regulatory environment: As governments worldwide develop frameworks governing digital assets’ transferability across borders—and increasingly scrutinize crypto exchanges—the regulatory landscape could impact how these bridges operate moving forward.*
Looking ahead:
The continued evolution will likely see further integration efforts driven by industry collaborations aiming at reducing risks while expanding functionality—for example through standardized protocols that enhance trustworthiness—and possibly integrating emerging technologies such as zk-rollups or optimistic rollups into bridge architectures.
By understanding how specific cross-chain bridges connect prominent blockchains like Solana (SOL), Ethereum (ETH),and Avalanche (AVAX), stakeholders—from developers to investors—can better navigate this rapidly evolving ecosystem while appreciating both opportunitiesand inherent risks involvedin multi-network operations
Penafian:Berisi konten pihak ketiga. Bukan nasihat keuangan.
Lihat Syarat dan Ketentuan.